Executive Summary
The Department of Homeland Security (DHS) needs substantial reform and improvement in order to fulfill its important roles in the areas of security, emergency preparedness and response, and enforcement of immigration laws. This will require changes in nearly every part of DHS, as well as a better prioritization of resources within each of the components and between the components. This executive summary provides key policy recommendations and corresponding budgetary changes for Congress to consider as it moves through the budgetary process.
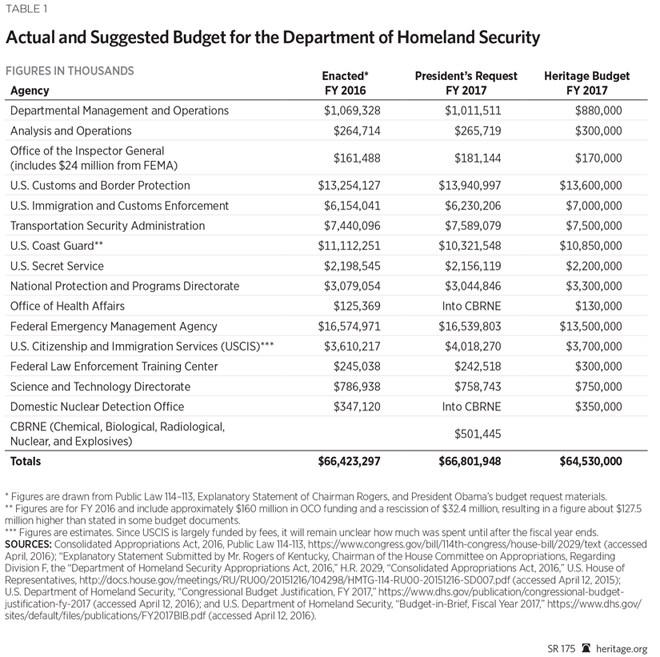
Department of Homeland Security Total Budget Authority
- DHS Total Budget Authority: approximately $64.5 billion.
- Increasing DHS management funding and strengthening the authority of DHS headquarters in order to improve the coordination, integration, and common situational awareness of DHS components: $880 million.
- Inspector General (IG) unchanged: $170 million.
- Refocusing the Office of Intelligence and Analysis (I&A) on sharing information with state, local, tribal, territorial, foreign, and private-sector partners; streamlining fusion centers; and supporting improved integration of information collected by DHS components: $300 million.
- Supporting increased Customs and Border Protection (CBP) infrastructure and technology and increasing patrols and equipment for CBP officers: $13.6 billion.
- Increasing Immigration and Custom’s Enforcement’s (ICE’s) budget to enable expansion of detention and effective alternatives to detention; expanding visa-overstay-removal operations; increasing the number of illegal immigrants removed; and defunding executive actions that weaken immigration enforcement efforts: $7 billion.
- Streamlining the Transportation Security Administration (TSA) to ensure the safe expansion of trusted-traveler programs and private airport screening, and decreasing costs while maintaining security and increasing efficiency: $7.5 billion.
- Expanding Coast Guard funding to support acquisition goals for additional ships and aerial platforms while meeting operational needs: $10.85 billion.
- Increasing Secret Service funding with the need for close oversight during this troubled time in the agency’s history: $2.2 billion.
- Strengthening the cybersecurity funding available to the National Protection and Programs Directorate and implementing improved cybersecurity and infrastructure protection policies: $3.3 billion.
- Significantly reforming each of the major parts of the Federal Emergency Management Agency (FEMA), including overhauling the Stafford Act to return responsibility for localized disasters to state and local governments, where they have been handled historically; consolidating and streamlining grants to have a risk-based focus; and fixing the National Flood Insurance Program that is draining U.S. tax dollars: $13.5 billion.
- Reforming U.S. Citizenship and Immigration Services (USCIS) funding to expand fraud prevention in the E-Verify and visa systems while defunding deferred-action memorandums that are unconstitutional and harmful to U.S. immigration law enforcement: $3.7 billion.
- Expanding the Federal Law Enforcement Training Center’s operations: $300 million.
- Prioritizing Science and Technology Directorate (S&T) research while encouraging private-sector research and development through the expansion of the Support Anti-Terrorism by Fostering Effective Technologies (SAFETY) Act: $750 million.
- Maintaining the Domestic Nuclear Detection Office (DNDO) and Office of Health Affairs (OHA): $350 million and $130 million, respectively.
Budget Summary for DHS Management and Inspector General (IG)
Policy Recommendations
- Create a more unified, standardized procurement and acquisitions process, and a more empowered Chief Procurement Officer, to drive these reforms.
- Provide more authority to centralized service components, such as the General Counsel, the Chief Financial Officer (CFO), the Chief Information Officer (CIO), and International Affairs, over their respective component offices. Such measures should not prevent component heads from exercising their authority, but should ensure that department-level directives are being carried out.
- Strengthen the DHS Policy Department to develop intra-agency policy, resolve disputes, and drive organizational change that makes DHS components work as a more cohesive unit.
- Link policy to planning, budget, and execution. This requires the development of homeland security doctrine, still lacking 14 years after the department began operation, and a headquarters-led program of Planning, Programming, Budgeting & Execution (PPBE). Most notably, more resources need to be put to the task; from strategic planning to program evaluation, the department systematically underinvests in self-analysis and evaluation.
- Streamline congressional oversight of DHS. As the Aspen Institute put it in 2013, “DHS should have an oversight structure that resembles the one governing other critical departments, such as Defense and Justice.” This means placing oversight of DHS under one primary homeland security committee in the House, and one in the Senate, with some additional oversight by the intelligence committees and a homeland security appropriations subcommittee in both chambers.
- Centralize DHS headquarters. Without a facility that can accommodate headquarters personnel and relevant component personnel, the integration and synergy of DHS suffers.
Funding
- The Heritage Foundation recommends $880 million in its proposed budget for departmental management and operations for achieving these recommendations.
- With no serious changes needed to the IG, Heritage recommends $170 million.
Budget Summary for DHS Intelligence Activities
Policy Recommendations
- Streamline U.S. fusion centers. Congress should limit fusion centers to the approximately 30 areas with the greatest level of risk as identified by the Urban Area Security Initiative (UASI). While exceptions might exist, such as certain fusion centers that lead cybersecurity or other important issue-specific efforts, the remaining centers should be fully funded and resourced by the UASI.
- Refocus DHS’s intelligence capabilities. Intelligence and information is critical to preventing terrorist attacks. Congress should consider redirecting DHS efforts toward information sharing and coordinating proper roles and responsibilities for federal, state, and local counterterrorism measures. Instead of replicating other intelligence efforts, I&A should use the unique data from DHS components.
- Ensure that the FBI more readily and regularly shares information with state and local law enforcement, treating state and local partners as critical actors in the fight against terrorism. State and local governments and private-sector partners must send and receive timely information to and from the FBI. DHS should play a role in supporting these partners, by acting as a source or conduit for information and coordinating information sharing between the FBI and its partners.
Funding
- Heritage recommends $300 million for analysis and operations to carry out these recommendations. Heritage also recommends additional funding for the FBI’s National Security and Intelligence branches.
Budget Summary for Customs and Border Protection (CBP)
Policy Recommendations
- End the 100 percent cargo-scanning mandate. Congress should reject this cost-inefficient measure and instead support DHS’s ongoing efforts to conduct risk-based scanning.
- End the biometric exit requirement. Biometric exit is another cost-ineffective solution that does nothing to combat visitors who overstay their visas, and has minimal counterterrorism benefits. Instead, the resources of this program should be spent improving a biographic exit system, improving other intelligence tools, and increasing ICE’s ability to remove visa overstays.
- Decouple the Visa Waiver Program (VWP) from the biometric exit requirement. The VWP enhances U.S. security, trade, and diplomacy and should not be connected to a biometric exit system. Instead, program enhancements to Electronic System for Travel Authorization (ESTA), a modernization of the TECS vetting and investigation management system, and a judicious VWP expansion will make the U.S. more secure and prosperous.
- Expand Global Entry reciprocity agreements. The U.S. should build on existing partnerships, not only among nations already participating in Global Entry, but also with VWP member countries, thus creating a trusted-travel superhighway that enhances security and facilitates travel.
- Improve border security technology and infrastructure. Improved technology on the border, together with targeted increases in fencing, infrastructure, and other resources for Border Patrol agents, will improve the effectiveness of the CBP.
Funding
- Heritage recommends $13.6 billion for the CBP.
Budget Summary for Immigration and Customs Enforcement (ICE)
Policy Recommendations
- Defund the President’s executive actions on immigration enforcement. The Obama Administration has issued a series of policy memorandums that do not allow ICE Enforcement and Removal Operations (ERO) officers to do their jobs. To improve morale and enforce existing immigration laws, Congress should not allow any funding to be used in support of these amnesty and non-enforcement policies. Failing to do so jeopardizes Congress’s constitutional authority and sets a dangerous precedent that empowers the executive branch in ways that all Americans should fear.
- Strengthen the 287(g) program. Designed to enable state and local government to help enforce federal immigration laws, 287(g) has been under assault during the Obama Administration, which has sought to cut funding, access to, and use of the program. Congress should seek to widen 287(g) usage by increasing funding for the program and requiring DHS to enter into a 287(g) agreement with any state and local governments that requests entry—with significant consequences, should DHS not meet this requirement in a timely fashion.
- Increase rapid-removal authority. Currently, Administration policy restricts ICE from removing many illegal border crossers in an expedited manner. To prevent future humanitarian and security crises on the border, ICE should be allowed to rapidly remove any illegal border crosser. This can be accomplished by making this authority explicitly clear in section 235 of the Immigration and Nationality Act of 1952, and by reforming the William Wilberforce Trafficking Victims Protection Reauthorization Act of 2008 to clarify that children who are not victims of human trafficking should also be removed in an expedited manner to discourage future surges.
- Provide more prosecutors and agents. In addition to cancelling non-enforcement policies and letting ICE agents do their jobs, Congress should increase the number of ERO officers as well as a corresponding number of prosecutors and legal personnel to increase and expedite removals.
- Increase the number of immigrants who appear at their court hearings. While more detention beds mean that more individuals will show up to immigration proceedings, this system can be expensive. Increasing the use of the most effective alternatives to detention (ATD), such as GPS tracking anklets, is a cost-effective way of reducing the number of absconders.
Funding
- Heritage recommends $7 billion for ICE.
- Heritage also recommends additional funding for Department of Justice immigration judges and support staff.
Budget Summary for the Transportation Security Administration (TSA)
Policy Recommendations
- Improve security assessments. In order to continue the judicious growth of TSA PreCheck and risk-based security, the TSA must conduct proper security assessments and refine the screening and vetting process to minimize security risks. Red team exercises should become a larger part of these assessments.
- Embrace risk-based screening. Measures, such as the Automated Targeting System, which subject cargo to a risk rating that determines whether it should be given additional screening, are the right way forward in terms of effective air cargo security. Congress and DHS should look for ways to move away from a blanket screening process. At a bare minimum, they should expand the Certified Cargo Security Program, which allows more flexibility in how the private sector may meet the 100 percent screening mandate. Congress and the TSA should also look to expand enrollment in TSA PreCheck to shorten airport security lines.
- Simplify the Screening Partnership Program (SPP) approval and contracting process. The process for joining the SPP should be streamlined to make it easier for airports to apply and make TSA adjudication faster, fairer, and more consistent. Airports joining the SPP should also be allowed to select and manage their own screening contractors from a list of TSA-approved companies instead of being micromanaged by the TSA.
- Limit collective bargaining. Collective bargaining in the screening line is harming security and costing taxpayers and travelers. Congress should expressly forbid the TSA from bargaining collectively.
- Expand the Federal Flight Deck Officers (FFDO) program. Greater funding for the FFDO program will enable this extremely cost-effective program to grow significantly.
- Review alignment of the TSA budget with the risks. TSA resources for any given activity should match the relative level of risk that that activity is working to mitigate. This requires that the TSA, its IG, or the Government Accountability Office (GAO) examine classified risk assessments and realign funding to better match the severity of different risks.
Funding
- Heritage recommends $7.5 billion for the TSA.
Budget Summary for the U.S. Coast Guard (USCG)
Policy Recommendation
- Recapitalize the U.S. Coast Guard. Funding for acquiring new Coast Guard vessels has been regularly short of what is necessary to complete the Coast Guard’s mission, and often results in additional acquisitions inefficiencies and costs. Congress should commit to providing the Coast Guard with consistent acquisitions funding so that the USCG will have the vessels it needs to complete its missions adequately. Congress should also ensure that any additional resources it provides to the Coast Guard are used to meet important priorities, including cost-efficient acquisition of the Fast Response Cutter (FRC), polar ice breakers, and unmanned systems.
Funding
- Heritage recommends $10.85 billion to the USCG:
- $1.5 billion for Acquisition, Construction, and Improvements (AC&I). This funding should include robust Offshore Patrol Cutter (OPC) development, more unmanned aircraft systems, and adequate funding for a cost-effective heavy-duty icebreaker capability.
- $7.06 billion for operating expenses. Fiscal year (FY) 2016 appropriations included $7.06 billion for operating expenses, including $160 million for Overseas Contingency Operations (OCO). The Heritage budget maintains this level of OCO funding for 2017.
- The USCG should maintain funding for other programs. Environmental compliance, reserve training, health care, retirement pay, and other programs are funded at levels requested by the President.
Budget Summary for the U.S. Secret Service (USSS)
Policy Recommendations
- Increase USSS staffing. The review panel recommended 85 more Presidential Protective Division (PPD) agents and 200 more officers, but called on the USSS to create a mission-based budget that will determine the appropriate staffing levels.
- Mandate increased training. The panel called for PPD agents to spend 25 percent of their on-duty time in training, the so-called Fourth Shift. For the other USSS officers, a minimum of 10 percent training time should be required.
- Require increased disciplinary and accountability standards. When improper behavior or mistakes are made, the USSS should demand a strict disciplinary or corrective action. Supervisors and managers must be made to uphold these standards or be made accountable themselves. Congress should require the GAO to report on how these standards are used and whether they are instilling discipline across the service.
- Expand the number of professional administrators, rather than agents or officers, responsible for budgeting and workforce functions. The review panel points out that agents and officers may not always be the best at completing administrative tasks, and that a larger suite of professional administrators could support and improve planning and execution of core responsibilities.
- Provide continued oversight to ensure that reforms are completed thoroughly.
Funding
- Heritage recommends $2.2 billion for the USSS.
Budget Summary for the National Protection and Program Directorate (NPPD)
Policy Recommendations
- Implement cyber-threat and cyber-vulnerability information sharing. Allowing the private sector and public sector to more easily share information with each other will benefit both sides. By providing strong liability protection for information that is shared, businesses are encouraged to share with the government as well as with other businesses.
- Help DHS improve and expand its ability to monitor government networks. The DHS-run “Einstein” intrusion-detection-and-prevention system has grown dramatically over the past decade. With better information sharing, Einstein’s ability to detect and prevent intrusions would be enhanced, but the system must always be improved as the nature of the threats change. DHS needs the clear authority, relationships, and ability to work with other agencies in using Einstein and other cyber tools.
- Improve morale of DHS staffers. Morale at the NPPD is incredibly low, which makes it difficult to recruit and keep good employees, especially when private-sector cybersecurity jobs are available. Notably, pay is not the central issue in this survey; the lack of leadership, training, and performance-based rewards are blamed and must be fixed. If DHS is to be an effective actor, it must do more to maintain a highly skilled workforce.
- Reform risk assessments to capture all relevant information, including consequences, threats, and vulnerabilities. DHS has a history of conducting risk assessments poorly, and this systemic problem must be resolved. Not correcting this problem means that important security decisions are made with inaccurate information. Trouble with risk assessments at the Federal Protective Service (FPS) and the Infrastructure Security Compliance Division severely hamper the efforts of the NPPD to secure critical infrastructure.
- Return the Chemical Facility Anti-Terrorism program to a truly risk-based approach. A risk-based approach would allow chemical facilities and DHS to prioritize their actions and resources to concentrate on threats that pose the most serious risks. This means ensuring that DHS expands the use of Alternative Security Programs, expedites security plan approvals, and improves risk assessments.
- Improve interoperable communications policies. The Office of Emergency Communications and coordinating bodies must receive more authority to inject policy into each DHS component. Policies must be improved to ensure that DHS radio users are able to seamlessly communicate with other federal officials, not to mention state and local partners.
- Explore alternative funding structures for the FPS. The GAO recommended comparing alternative funding structures to ascertain the pros and cons of different approaches that include some level of direct appropriation. Inserting a more stable source of income might improve the FPS’s budgeting and planning processes as well as improve the way it provides training to its officers. This should be explored by the FPS and the Congressional Research Service.
Funding
- Heritage recommends $3.3 billion for the NPPD.
Budget Summary for the Federal Emergency Management Agency (FEMA)
Policy Recommendations
- Reduce the federal share for all FEMA declarations to 25 percent of total cost per declaration. This way, at least three-fourths of the costs of a disaster are borne by the taxpayers living in the state or states where the disaster took place. For catastrophes with a nationwide or widespread regional impact—such as Hurricane Katrina—a relief provision would provide a higher federal cost share if the total costs of the disaster exceeded an inflation-adjusted threshold.
- Modify the Stafford Act to establish clear requirements that limit the situations in which FEMA can issue declarations. One way to do this is to raise the minimum-dollar threshold for requesting disaster declarations. Increasing the per capita threshold to $3 and properly indexing these sums for inflation would significantly reduce the number of events that would warrant a federal disaster declaration.
- Consolidate homeland security and emergency-preparedness grant programs and allocate funds in a risk-based manner. Rather than treating grants as federal dollars to be spread around, federal grant dollars should be focused on the highest-risk areas and issues. As part of this consolidation, grant programs should be evaluated, and ineffective ones— such as Staffing for Adequate Fire & Emergency Response (SAFER), Fire Prevention & Safety (FP&S), and Assistance to Firefighters Grants (AFG)—should be cancelled.
- Begin to transition nearly all users of the National Flood Insurance Program (NFIP) to private insurance. The NFIP should be wound down. Within one year, the NFIP should begin ending insurance for lower-risk insured groups, followed by phasing out NFIP insurance for increasingly high-risk properties. Within four years, the NFIP should only exist to serve a select few homeowners who are unable to acquire insurance, not because the cost is too high, but because it is not offered where they live. These properties, however, should pay a rate that is as actuarially fair as possible.
Funding
- Heritage recommends $13.5 billion for FEMA.
Budget Summary for U.S. Citizenship and Immigration Services (USCIS)
Policy Recommendations
- Reject political influence in the visa-adjudication process. When executive policymaking forces USCIS employees to cut corners, and high-ranking politicos are able to wield their influence to obtain green cards for their friends and businesses, the U.S. effectively has a two-tier immigration system—one that serves the well-connected and special interests, and one that deals with everyone else. Good governance requires that this sort of corruption end. Congress should require the Inspector General to conduct ongoing investigations into the way political influences are pressuring USCIS employees to bend the rules.
- Restart comprehensive immigration-fraud evaluations. The U.S. is a generous nation that provides many people with immigration benefits, but there are many who abuse the system. Given the value of U.S. visas and citizenship, the U.S. should do more to investigate fraud, both on a case-by-case basis, and through more complete assessments and investigations.
- Strengthen E-Verify against identity theft. E-Verify prevents unauthorized individuals from being hired, but one flaw of the system is that those who use legitimate Social Security numbers acquired through identity theft can be authorized. The Social Security Administration should be required to work with the E-Verify system to identify cases where Social Security numbers are being used in multiple places or in suspicious ways.
- Reform the USCIS’s funding mechanism. To help the USCIS conduct more fraud prevention, acquire better IT systems such as the Electronic Immigration System, and improve other administrative functions, the USCIS funding model should be changed. Currently, only E-Verify is funded by appropriations. Congress should move administrative parts of the agency to more regular appropriations to ensure that basic functions are not funded according to visa revenues.
- Ensure refugee resettlement is secure. Congress should continuously demand risk assessments regarding the resettlement of refugees and how the administration is managing that risk. Congress should also push USCIS to enhance the training and expertise of USCIS refugee officers as well as updating and improving DHS’s vetting and immigration systems.
- Promote real assimilation. Becoming an American should be a meaningful experience that instills immigrants with a love of America and her values. Current integration efforts portray citizenship as little more than a right to a U.S. passport. The USCIS must retool its integration measures, and, instead of emphasizing multiculturalism, diversity, and political activism as the desired values, promote patriotism, American principles, and civic education.
Funding
- Heritage recommends $3.7 billion for the USCIS.
Budget Summary for the Federal Law Enforcement Training Center (FLETC)
Policy Recommendations
- Expand training for state and local law enforcement. Since state and local law enforcement officers are often the first to respond and deal with a crisis, such as an active shooter, DHS should expand “train the trainer” programs and direct training of state and local officers.
- Consolidate training facilities under the FLETC. DHS should act on multiple studies recommending ways to consolidate additional facilities into the FLETC. As part of that consolidation, Congress should require a study to see if other training facilities planned for or operated by other agencies could be consolidated and operated by the FLETC.
Funding
- Heritage recommends $300 million for law enforcement training.
Budget Summary for DHS Research and Development (R&D) Organizations
Policy Recommendations
- Develop clear policies for overseeing R&D. With S&T only recently defining what R&D is, S&T and other DHS components must properly report and account for spending on their research activities. This should feed into a mechanism for tracking R&D projects and total expenditures. While S&T has taken preliminary steps to assign roles and responsibilities for coordination of R&D projects, Congress should oversee these new guidelines to ensure that relevant agencies are fulfilling their responsibilities.
- Reject inserting pork into R&D missions. R&D is a common area in which Congress mandates certain pork-barrel projects that benefit parochial interests in Members’ districts regardless of the wisdom of such an investment. While Congress can and should oversee spending, it should not insert political and parochial interests to the detriment of R&D.
- Focus on primary customers—DHS components. While S&T’s efforts can have benefits for state, local, and private-sector needs, S&T should focus on meeting the needs of DHS components first and foremost.
- Formalize relationships between S&T and other components. To better coordinate research and meet component needs, Congress should more formally connect S&T with research and requirement-setting activities. At a high level, this means the creation of a formal oversight council or process to ensure that S&T and relevant parties share visibility and understanding of research projects. At a lower level, this means expanding initiatives, such as Apex programs, which involve integrating component staff in the S&T R&D process to increase research usefulness to end users.
- Expand the SAFETY Act. One way to support the development of products that support end-user needs is to expand the Support Anti-Terrorism by Fostering Effective Technologies (SAFETY) Act, as profit is a good incentive for developing products and services that meet user needs. By expanding the SAFETY Act’s protections in a reciprocal nature with other nations, the U.S. will have access to even more lifesaving technologies. Congress should start a pilot program with a willing ally, such as Israel, to work out the details.
Funding
- Heritage recommends:
- $750 million to S&T.
- $350 million for the DNDO.
- $130 million for the OHA.
In 2015, the Department of Homeland Security (DHS) had a total budget authority of $63.5 billion—which grew to $66.3 billion in 2016.[1] This budget funds a diverse set of agencies responsible for a wide range of issues: counterterrorism, transportation security, immigration and border control, cybersecurity, and disaster response. Yet, DHS’s management of these issues is highly flawed, both in the finer details of its operations and its broader priorities. Such failure has provoked a small chorus to question the value of DHS as a whole and whether the U.S. would be better served without it. Serious changes across all of its policy areas, a realignment of its priorities, and reform of the way DHS headquarters operates are imperative to fixing DHS.
Through the budgeting process, Congress has legislative authority to reform DHS. It can and should use its budgetary authority to expand some programs, alter others, and shrink or defund those programs that are flawed, inefficient, or low priorities. DHS does not need more funding—it needs better prioritization of its funding. The Heritage Foundation has constructed a complete reform agenda and an alternative, $64.5 billion budget that proposes:
- Increasing DHS management funding and strengthening the authority of DHS headquarters to improve the coordination and integration of all DHS components;
- Refocusing the Office of Intelligence and Analysis on sharing information with state, local, tribal, territorial, foreign, and private-sector partners; streamlining fusion centers; and supporting improved analysis and integration of information collected by DHS components;
- Supporting increased Customs and Border Protection (CBP) infrastructure and technology; increasing patrols and equipment for CBP officers; and updating the CBP’s information-sharing system, TECS;
- Increasing the budget of Immigration and Customs Enforcement (ICE) to enable expansion of detention and effective alternatives to detention; expanding visa-overstay-removal operations; increasing the number of illegal immigrants who are removed; and defunding executive actions that weaken immigration enforcement;
- Streamlining the Transportation Security Administration (TSA) to ensure the safe expansion of trusted-traveler programs and private airport screening, decreasing costs while maintaining security and increasing efficiency;
- Expanding Coast Guard funding to support acquisition goals for additional ships and aerial platforms;
- Increasing Secret Service funding and training, with emphasis on better oversight during this troubled time in the agency’s history;
- Increasing the cybersecurity funding for the National Protection and Programs Directorate (NPPD), and implementing improved cybersecurity and infrastructure-protection policies;
- Significantly reforming each of the major parts of the Federal Emergency Management Agency (FEMA), including overhauling the Stafford Act to return responsibility for localized disasters to state and local governments, where they have historically been handled; consolidating and streamlining grants toward a risk-based focus; and reforming the National Flood Insurance Program (NFIP) that is draining U.S. tax dollars;
- Reforming U.S. Citizenship and Immigration Services (USCIS) funding to expand fraud prevention efforts in the E-Verify and visa systems while defunding deferred-action policies that are unconstitutional and harmful to U.S. immigration law enforcement;
- Expanding the Federal Law Enforcement Training Center’s (FLETC’s) operations and availability; and
- Prioritizing Science and Technology Directorate (S&T) research while encouraging private-sector research and development through the expansion of the Support Anti-Terrorism by Fostering Effective Technologies (SAFETY) Act of 2002.
While Congress may be hesitant to flex its budgetary muscles after surrendering to the executive branch on a DHS continuing resolution for fiscal year (FY) 2015, Congress must use this power, or else become a mere rubber stamp for executive action or inaction, not to mention continued program and policy problems and failures. U.S. security and safety, the rule of law, and limits on the executive are all at stake in the budgeting process, and it is past time that the first branch of government exercise its constitutional authority to make major reforms to DHS.
1. Management
DHS management and headquarters received a significant increase in FY 2016, from around $743 million in FY 2015 to $1.12 billion in the FY 2016 appropriation. This increase includes several large sums from the general provisions section of the DHS appropriations, including $50 million for counterterrorism funding, $100 million for improving DHS cybersecurity systems and capabilities, $53 million for modernizing the financial system, and $216 million to build the new DHS headquarters building.[2] This funding increase is not entirely uncalled for. DHS faces a number of challenges that it has yet to adequately address. DHS has been given a difficult mission and it has not yet been able to achieve the synergies required to carry out that mission. A key reason for this is DHS’s failure to fully integrate its management structure. The Government Accountability Office (GAO) has characterized the Homeland Security Department this way:
The Department of Homeland Security’s (DHS) efforts to strengthen and integrate its management functions have resulted in it meeting three and partially meeting two of GAO’s criteria for removal from the high-risk list…. However, DHS needs to show additional results in other areas, including demonstrating the ability to achieve sustained progress across 30 outcomes that GAO identified and DHS agreed were needed to address the high-risk area. As of March 2016, DHS had fully addressed 10 of these outcomes but work remained in 20.[3]
In DHS’s management of acquisitions, the GAO found that while component acquisition capabilities were improved, major concerns remain over the number of trained acquisition personnel at headquarters and component levels, and the ability to determine “that major acquisition programs are on track to achieve their cost, schedule, and capability goals.”[4] The GAO also reported serious problems with DHS financial management, finding serious deficiencies in departmental and component financial management systems despite recent improvements. The GAO described these problems as representing “long-term challenges in obtaining and sustaining a clean audit opinion on internal control over financial reporting, and ensuring its financial management systems generate reliable, useful, and timely information for day-to-day decision making.”[5] The GAO also found problems in DHS’s management of information technology and technology integration, including problematic component-level adoption of some elements of headquarters’ IT plans, information security, headquarters’ financial-reporting systems, and the need for sustained progress in its integration of management efforts across the department.
The GAO report also described widespread human capital and morale issues that plague the department. The Office of Personnel Management’s (OPM’s) 2014 Federal Employee Viewpoint Survey “showed that DHS’s scores continued to decrease in all four dimensions of the survey’s index for human capital accountability and assessment—job satisfaction, talent management, leadership and knowledge management, and results-oriented performance culture.”[6] The 2015 survey showed that DHS continued its decline across the board, a four-year downward trend for the department.[7] According to the yearly survey conducted by the Partnership for Public service, DHS is currently the worst large agency in the federal government for which to work—far worse than the second-worst agency, the scandal-ridden Department of Veterans Affairs.[8] Seven of the 10-lowest-ranked subcomponents for which to work are within DHS. The Office of the Secretary and the Management Directorate score at 283 and 306, respectively, out of 320 agency subcomponents. These organizations do not all have morale problems by coincidence—the mismanagement of DHS is causing the department to suffer. Fourteen years after the creation of DHS, excuses must stop, and serious improvement must start.
DHS management issues, however, cannot be entirely blamed on DHS. The labyrinthine web of congressional oversight of DHS is sucking up DHS’s time and resources and providing duplicative or contradictory oversight. There is bipartisan agreement amongst former and current DHS officials, think tanks, and the 9/11 Commission that the current byzantine system of congressional oversight of DHS is harming security due to power politics.[9] There is no reason for jurisdiction over DHS to be split across about 100 committees and caucuses other than congressional Members’ unwillingness to give up a small slice of their power in exchange for improved security and efficiency. There is no disagreement on this matter. And so the chorus of experts continues to beg Congress to do the right thing and finally put security before politics.
Actions for Congress. Building on the recommendations of the GAO and others, Congress should undertake non-flashy, but important, reforms of DHS management systems and processes. Congress should:
- Create a more unified, standardized procurement and acquisitions process, and empower the Chief Procurement Officer to drive these reforms.
- Provide more authority to centralized service components, such as the General Counsel, the Chief Financial Officer (CFO), the Chief Information Officer (CIO), and International Affairs, over their respective component offices. Such measures should not exclude component heads from exercising their authority, while ensuring that department-level directives are being carried out.
- Strengthen the DHS Policy Department to develop intra-agency policy, resolve disputes, and drive organizational change that makes DHS components work as a more cohesive unit.
- Link policy to planning, budget, and execution. Such linking requires the development of homeland security doctrine, still lacking more than 14 years after the department began operation, and a headquarters-led program of Planning, Programming, Budgeting & Execution (PPBE). Most notably, more resources need to be put to the task; from strategic planning to program evaluation, the department systematically under-invests in self-analysis and evaluation.
- Streamline congressional oversight of DHS. As the Aspen Institute put it in 2013, “DHS should have an oversight structure that resembles the one governing other critical departments, such as Defense and Justice.”[10] This means placing oversight of DHS under one primary homeland security committee in the House and the Senate with some additional oversight by the Intelligence Committees and a homeland security appropriations subcommittee in both chambers.[11]
- Centralize DHS headquarters. Without a facility able to accommodate headquarters personnel and relevant component personnel, the integration and synergy of DHS suffers.
To fund these activities, The Heritage Foundation recommends $880 million.
Analysis and Operations
With $252 million in FY 2015 and $265 million in FY 2016, President Obama requested $265 million again in FY 2017 for Analysis and Operations activities. Many details concerning Analysis and Operations are classified and receive National Intelligence Program (NIP) funding. Created after 9/11, DHS’s raison d’être was to better prepare the U.S. for combatting terrorism. To this end, DHS, in addition to components such as the CBP, began to analyze and use information to prevent threats to the U.S. before they materialize. Thus, the Office of Intelligence and Analysis (I&A) and the Office of Operations Coordination (OPS) were created. DHS, however, was not to become a full-fledged domestically focused intelligence organization, with the FBI given that responsibility instead after 9/11. As a result, DHS’s role in the intelligence arena remains limited. It does, however, have unique access to a variety of travel and immigration information, which it can provide to other agencies.
The nature of the terrorist threat has changed over time and grown more serious. With the rise of ISIS and other Islamist groups in Syria, the U.S. has seen a dramatic increase in terrorist activity at home. In 2015, the U.S. faced 17 Islamist terror plots and attacks, more than any other year since 9/11. At the time of this writing, the U.S. already had 12 terror plots and attacks in 2016, bringing the total to 93 since 9/11. FBI Director James Comey agrees that, given the escalation of foreign fighters and those who seek to join a radical Islamist group in Syria, the U.S. is facing more terrorist threats to the homeland now than any time since 9/11,[12] a sentiment echoed by other leading intelligence and law enforcement officials.[13]
Given this threat, it is critical that the U.S. make the most of its counterterrorism resources. In 2012, the Senate Homeland Security and Government Affairs Committee found that fusion centers “often produced irrelevant, useless or inappropriate intelligence reporting to DHS and many produced no intelligence reporting whatsoever.” It also provided multiple assessments and examples that show that fusion centers are not meaningfully contributing to counterterrorism measures and may have even been harming them.[14] A more recent report by the RAND Corporation also found that fusion centers have mixed results and often serve different purposes.[15] Meant to serve as hubs of cooperation between federal, state, and local officials, 78 fusion centers often serve cities or regions already covered by 104 FBI Joint Terrorism Task Forces (JTTFs) and 56 Field Intelligence Groups (FIGs), which play a similar role to that of fusion centers.[16] This broad duplication of efforts results in an inefficient and counterproductive use of counterterrorism funds.
In 2013, the DHS Inspector General (IG) reported that DHS’s Homeland Security Information Network (HSIN)—designed to share sensitive but not classified information with federal, state, and local governments and private-sector partners—was only being used by a small percentage of all potential partners. State and local officials stated that one reason for not using the HSIN was that “the system content was not useful.”[17] Since the IG report came out, however, the HSIN has successfully migrated to an updated system and is seeking to add desired content from DHS components and attract more users. At around 36,000 active users at the end of 2014, the HSIN is far short of an Office of Management and Budget target for 2015 of 130,000 users. However, since the move to the new HSIN system, this seems to have improved, with 65 percent of respondents in 2014 saying that HSIN met their needs at least most of the time, with 83 percent of respondents using HSIN at least weekly.[18]
I&A also faces other challenges, such as with its workforce. A 2014 GAO report found that I&A was slower in hiring applicants than other agencies in the intelligence community, harming DHS’s ability to attract talent. The GAO noted that this has resulted in a “reliance on contractors to fill the gaps in Intelligence Community experience.”[19] The GAO also noted I&A’s professional development challenges and high levels of attrition in its workforce. Such difficulties have certainly helped cause, and have been caused, by low morale, as I&A was rated the worst office for which to work in the federal government in 2015.[20]
Actions for Congress. To better protect the U.S. from terrorism, Congress should:
- Streamline U.S. fusion centers. Congress should limit fusion centers to the 28 areas with the greatest level of risk as identified by the Urban Area Security Initiative (UASI).[21] Some exceptions might exist, such as certain fusion centers that are leading cybersecurity or other important topical efforts. These centers should then be fully funded and resourced by the UASI.
- Refocus DHS’s intelligence capabilities. Intelligence and information is critical to preventing terrorist attacks. Congress should consider redirecting DHS efforts toward information sharing and coordinating proper roles and responsibilities for federal, state, and local counterterrorism. Instead of replicating other intelligence efforts, I&A should also focus on using its unique data from DHS components.
- Ensure that the FBI more readily and regularly shares information with state and local law enforcement, treating state and local partners as critical actors in the fight against terrorism. State and local governments and private-sector partners must send and receive timely information from the FBI. DHS should play a role in supporting these partners’ efforts by acting as a source or conduit for information between partners and coordinating information sharing between the FBI and its partners.
To fund these activities, the Heritage budget recommends $300 million for analysis and operations. Heritage also recommends additional funding for the FBI’s National Security and Intelligence branches.
2. Inspector General
For FY 2016, approximately $161 million was budgeted for the Inspector General. President Obama’s FY 2017 budget requested $181 million. With no serious changes needed to the IG, Heritage recommends $170 million.
3. Customs and Border Protection
Approximately $13.25 billion was budgeted in FY 2016 for CBP; President Obama requested $13.94 billion for FY 2017. CBP is the largest DHS component by budget and full-time workers. Its primary activities consist of security and inspection of travelers and goods at U.S. ports of entry (POE), including seaports, airports, and land-border crossings, as well as border security between those POEs. While CBP could use targeted investments, the U.S. should not throw away fiscal discipline.
At POEs, CBP currently struggles with several unwieldy mandates, including a requirement to scan 100 percent of containers arriving in the U.S. by sea, and a biometric exit mandate for visitors to the U.S. The scanning requirement means that 100 percent of sea cargo bound for the U.S has to be scanned by radiation detection and imaging technologies before being sent to the U.S.[22] This mandate has been delayed twice due to cost and technology concerns that seem insurmountable. Indeed, the most recent information from CBP in 2011 indicated that only 1 percent of cargo was scanned overseas and another 4 percent was scanned here in the U.S.[23] Even if the money and technology did exist, funding spent on 100 percent scanning could be better spent on intelligence tools that ascertain which cargo shipment is high risk, and subjecting that cargo to additional scrutiny and scanning. Full implementation of the scanning mandate will not only entail costs for CBP, but would also entail delays and costs to the global supply chain, foreign nations, and U.S. consumers, since more than 10 million containers enter the U.S. every year.[24]
On the other hand, the 100 percent biometric exit requirement is focused on visitors leaving the United States. Currently, the U.S. accepts biometric (fingerprint) and biographic (names) information for inbound visitors and uses that data to cross-check against various terror, law-enforcement, and immigration watch lists and systems. The U.S., however, has only a biographic exit system, despite a requirement for a biometric exit system since the Intelligence Reform and Terrorism Prevention Act of 2004. Once again, technology, cost, and logistics concerns have made the implementation of such a system difficult at airports, not to mention the statutory requirement for use at all POEs including sea ports and land ports.[25] While a biometric exit system may be slightly more accurate and helpful than a biographic one, it is not currently cost-effective in combatting illegal immigration or terrorism—the dollars spent on a biometric exit system would be better spent improving the biographic system and increasing immigration enforcement and intelligence capabilities.
The biometric exit mandate is also a road block to the expansion of the Visa Waiver Program (VWP), which enhances security and promotes travel. The VWP allows residents of member countries to visit the U.S. without a visa for up to 90 days in exchange for security cooperation and information sharing, and reciprocal travel privileges for U.S. residents. With more intelligence, the U.S. is better able to stop bad actors and terrorists, and it allows the existing visa process to focus its consular and visa resources on those individuals about whom less is known and those who are higher risks to U.S. security.[26] Despite unfounded security concerns, the VWP screens individuals through multiple systems, such as its TECS system that queries multiple security databases, including the Terrorist Screening Database.
Indeed, following the terrorist attacks in San Bernardino and Paris, Congress added various restrictions to the VWP, including denying VWP status to those who had visited certain countries (Iraq, Iran, Syria, or Sudan), or who hold dual citizenship in one of these countries. While some of the other steps regarding e-passports and expanded cooperation with other countries on airport and travel security were good additions, the additional restrictions do little to mitigate the risks of terrorism. For example, dual citizenship is a weak indicator of risk, considering that some countries, such as Iran, do not let their citizens forfeit citizenship, even if they received citizenship through their emigrated parents and have never so much as visited Iran. Furthermore, for DHS to stop such dual citizens from using the VWP, it relies on those same individuals to self-report their dual citizenship on the Electronic System for Travel Authorization (ESTA) application—something about which a knowledgeable terrorist or criminal would simply lie. Instead, this provision has had, and will have, harmful side effects for aid workers, journalists, businessmen, and dissidents and their children. Similarly, using travel to Syria as a disqualifier for using the VWP punishes those whose travel the U.S. knows about, but does nothing to stop a terrorist who snuck into Syria and, since his travel was undetected, is still allowed to use the VWP.
Expansion of this program has been extremely limited due to linking the biometric exit mandate to VWP expansion. These two programs should be unlinked, and Congress should remove the biometric exit requirement.
CBP also manages several trusted-traveler programs[27] that require a background check and include PreCheck benefits for U.S. citizens and permanent residents; these programs also provide expedited immigration and customs processing at airports or land borders, depending on the specific program.[28] The Global Entry program is open to U.S. citizens and permanent residents as well as citizens from six other nations, including Germany and South Korea, which allow U.S. citizens to join an equivalent program. The NEXUS program provides U.S. and Canadian citizens and residents with expedited processing when travelling between the two countries, while the SENTRI program expedites processing through land ports of entry on the southern U.S. border.[29] Reciprocal agreements, such as those through Global Entry, should be expanded to provide both the U.S. and its allies with the security and convenience of trusted-traveler programs.[30]
CBP’s other major duty is border security, carried out by the Border Patrol. During the summer of 2014, a surge of children and families from El Salvador, Honduras, and Guatemala stretched DHS resources, including CBP’s. The failure of successive Administrations to secure the border and enforce immigration laws have come to a head under President Obama, creating an incentive for yet more illegal immigration from the south. Together with widespread poverty and violence in these Northern Triangle countries, last summer was a perfect storm of events leading to a border crisis. The Obama Administration responded by allowing most families and children to remain in the U.S., sending them to various destinations across the U.S. to await full immigration proceedings. Rather than use its authority to rapidly return recent illegal border crossers to their home countries, as allowed under section 235 of the Immigration and Nationality Act, the Administration’s response resulted in additional costs across the immigration system.[31] Furthermore, the near complete failure to enforce U.S. immigration laws, as described in the “Immigration and Customs Enforcement” and “U.S. Citizenship and Immigration Services” sections below, is only encouraging additional illegal immigration, which makes the Border Patrol’s job that much more difficult. An increasingly difficult job beset by the policies adopted by organizational leaders and the President are cutting into organizational morale, with CBP dropping to 314 of 320 subcomponents in 2015 surveys on employee morale.[32]
Additional resources should be focused on improving the infrastructure, resources, and technology available to CBP to apprehend illegal immigrants and prevent entry of those who could pose a risk to the U.S.
One infrastructure improvement would be more secure fences along the southern border.[33] In 2006, President George W. Bush signed into law the Secure Fence Act, which called for approximately 700 miles of new fencing along the southern border.[34] DHS has put up the fencing, but the majority of it does not stop foot traffic, with much of the fencing being anti-vehicle “fencing” that is little more than metal poles or bars sunk into the ground every few feet. While some discretion in deciding what kind of fencing to use is appropriate, the U.S. would have a more secure border if double-layered fencing was installed to prevent pedestrian border crossers, as envisioned by the Secure Fence Act. These fences would be especially helpful in areas with a U.S. city or suburb on the other side of the border, which make it easy for illegal border crossers to fade into the background. But in addition to fences, facilities for processing incoming travelers, adjudicating immigration claims, and other customs and immigration tasks should also be considered.
While fences are important, they are far from a silver bullet—there are always alternative ways to entering and remaining in the country illegally. Increasing the amount of technology and wide-area surveillance technology available to the Border Patrol can make it more effective at finding and stopping border crossers. While past programs, such as the Secure Border Initiative Network (SBInet), have had technical problems, the concept—a network of surveillance technologies to watch the border—is a sound one. Rather than reinventing the wheel, DHS should borrow from the experiences and technologies of the U.S. military and its need for persistent, wide-area surveillance technologies in Iraq and Afghanistan. These systems are already in production, and using and adapting these systems would allow DHS to avoid the expensive development of new systems. With troops and their systems returning home, DHS may even be able to make use of surplus systems that the military does not need. The military would likely be able to provide training and support to DHS in setting up and operating these systems.
Actions for Congress. To improve U.S. efforts to protect the U.S. border and facilitate trade and travel without sacrificing security, Congress should make the following reforms to CBP:
- End the 100 percent cargo-scanning mandate. Congress should reject this cost-inefficient measure and instead support DHS’s ongoing risk-based scanning programs, focusing scanning resources on cargo that is considered highest-risk.
- End the biometric exit requirement. Biometric exit is another cost-ineffective solution that does nothing to stop visitors who overstay their visas. While biometric exit has minimal counterterrorism benefits, the resources that would be spent on this program should be spent on improving a biographic exit system, improving other intelligence tools, and increasing ICE’s ability to remove visa overstayers.
- Decouple the Visa Waiver Program (VWP) from the biometric exit requirement. The VWP enhances U.S. security, trade, and diplomacy and should not be connected to a biometric exit system. Instead, program enhancements to the Electronic System for Travel Authorization (ESTA), a modernization of the TECS vetting and immigration system, and a judicious VWP expansion will make the U.S. more secure and prosperous.
- Expand Global Entry reciprocity agreements. The U.S. should build on existing partnerships, not only with nations already participating in Global Entry, but also with VWP member countries, thus creating a trusted-traveler superhighway that enhances security and facilitates travel.
- Improve border security technology and infrastructure. Improved technology on the border, together with targeted increases in fencing and other resources for Border Patrol agents, will improve the effectiveness of the Border Patrol.
To fund these activities, the Heritage budget recommends $13.6 billion for CPB.
4. Immigration and Customs Enforcement
One of the most troubled agencies throughout the U.S. government, ICE had a budget of around $6.15 billion in FY 2016, and the President’s FY 2017 request would give ICE $6.23 billion in total budget authority. In addition to greater funding, ICE is in desperate need of major policy changes to boost morale and effectiveness.
Composed of two field divisions, Homeland Security Investigations (HSI) and Enforcement and Removal Operations (ERO), as well as Management and Administration and the Office of the Principal Legal Advisor, HSI and ERO maintain largely separate priorities. HSI focuses on combatting transnational crime and trafficking, international visa security, countering fraud operations, customs and intellectual property rights enforcement, and antiquities and art operations. As an organization more closely resembling traditional criminal law enforcement, HSI is largely free to pursue these goals. ERO, on other hand, is intended to focus on removing illegal immigrants, as well as legal immigrants and temporary workers who have committed a crime or are removable for another reason. ERO, however, is largely forbidden from pursuing the very objective for which it is intended. Numerous policies and pressures are placed on ICE agents to prevent them from enforcing the law. Ranging from the Morton Memos in 2011[35] to the Deferred Action for Childhood Arrivals Program, to enforcement “priorities” and the Deferred Action for Parents of Americans (DAPA) in the President’s executive action, ICE agents have been ordered to avoid enforcing the law against almost all illegal immigrants other than the most serious criminals.[36] The result is that once an individual overstays a visa or makes it past the border, it is unlikely that ICE will ever find or enforce the law against him.
Indeed, deportations of individuals from the U.S. interior have cratered in the past several years. DHS statistics indicate that the U.S. conducted only 462,463 removals and returns, known to the average American as deportations, in FY 2015, plummeting to their lowest level since 1971.[37] Deportations from the interior of the U.S. dropped from around 230,000 in FY 2010 to approximately 70,000 in FY 2015, a decline of 70 percent in just five years.[38] Even though removing criminal aliens is an Administration “priority,” ICE deported just over 63,000 criminal aliens from the U.S. interior in 2015, a decline of almost 60 percent from the 150,000 deported in FY 2011.[39] With deportations falling further, ICE is set to break more historical records on how few illegal immigrants it can deport.
The consequence of such action is that in the Partnership for Public Service’s 2014 annual survey, ICE was rated the worst organization in the federal government for which to work, with a steady downward trend since 2010 that corresponds with the Obama Administration’s actions on immigration. In 2015, ICE’s score fell further, but other DHS subcomponents fell even more, making ICE the third-worst place to work in the federal government.[40] There are few things more disheartening than signing up for a job and being dedicated to its mission and then not being allowed to do it. This is precisely the position in which ICE officers, especially in ERO, find themselves.
Furthermore, many foreigners who are in the U.S. illegally do not appear at their own court hearings for their deportation proceedings. According to the Department of Justice’s Executive Office of Immigration Review, 34 percent of non-detained aliens (illegal or legal) absconded from the court in FY 2014, rising to 43 percent in FY 2015.[41] Testimony by Brandon Judd, president of the National Border Patrol Council, which represents 18,000 Border Patrol agents, recently testified that DHS policy now requires Border Patrol agents to release, without any notice to appear in court, anyone they catch who has not been convicted of a felony so long as he claims to have been in the U.S. since January 2014.[42] Such “catch and release” policies further undermine the enforcement of U.S. immigration laws and artificially deflate the absentia rates by never including deportable aliens in the immigration process to begin with. If the U.S. is serious about stopping those who abscond, it should seek to increase the number of detention beds available, increase the use of effective alternatives to detentions (ATD) including GPS tracking anklets, and do more to ensure that ICE and DOJ immigration officials have—and use—the resources and tools to more rapidly remove illegal border crossers and visa overstayers.
The Obama Administration has also crippled state and local enforcement of immigration laws. Despite the importance of federalism to the U.S., the Obama Administration has attacked states that have taken action that comports with the letter and intent of federal immigration law. Utah, South Carolina, Alabama, and, most notably, Arizona, have all passed immigration laws that attempt to allow state and local officials to check the immigration status of individuals stopped in the due course of lawful police actions, and otherwise help federal authorities enforce U.S. immigration laws.
In a case ultimately argued before the Supreme Court, the U.S. government asserted that federal enforcement policies pre-empted Arizona’s 2010 immigration law, S.B. 1070, despite the fact that Arizona’s law was based on federal law. The U.S. government argued that its enforcement priorities and policies were the supreme law and that even if they deviated from the clear meaning and letter of the law, states had no right to enforce federal law since such enforcement deviated from the federal government’s policies.[43] This line of argument turns jurisprudence on its head, as it establishes not the law, but any given Administration’s preference as the supreme law of the land—dangerous territory for a nation that depends on the rule of law.
Five justices at least partially agreed with such a notion. While the Supreme Court upheld the vast majority of S.B. 1070, the court did reject three measures despite their clear basis in federal law. The Supreme Court did, however, affirm that states have an important role to play in enforcing federal immigration law: The court confirmed the ability of states to pass laws like S.B. 1070 that make it a state crime to engage in human smuggling, to hire illegal day-laborers on the roadside, or to encourage an individual to illegally cross the border, as well as requiring state law enforcement officers to check the immigration status of anyone they stop or detain where there is reasonable suspicion that the person might be in the country illegally.[44]
States like Arizona, which are experiencing significant problems with illegal immigration, or that are frustrated by the federal government’s lack of enforcement, are trying to step up and assist in enforcing immigration law. Just as state and local law enforcement resources should be and are used to combat terrorism due to the amount of state and local resources scattered across the U.S., so, too, should state and local government be partners in enforcing immigration law. With approximately 1.2 million state and local law enforcement officers and staff serving across the nation, the U.S. would be foolish to not take advantage of their local knowledge and presence.
Congress has created multiple programs that make use of local law enforcement, including the 287(g) program, Operation Stonegarden grants, and the Border Enforcement Security Task Force (BEST) units. Each of these programs serves an important purpose and, together with independent state efforts, helps to enforce U.S. immigration law more effectively. The Obama Administration has consistently rejected, cut funding for, fought, or limited many of these cooperative programs and state efforts. A central tenet of the Obama Administration has been to centralize power within the federal government, and nowhere is this truer than in immigration policy, where the executive branch has argued that it alone can enforce, or refuse to enforce, federal law. State and local officials are willing to volunteer to be trained to help enforce federal immigration law, but the executive branch has rejected their help and gone to budgetary and administrative extremes to combat local assistance in enforcing immigration law.
More specifically, the Secure Communities, 287(g), and similar programs have been used only to the extent that they advance the enforcement priorities of this Administration. For example, Secure Communities requires the FBI to provide DHS with a copy of the fingerprint and criminal records of individuals who are picked up by local and state law enforcement officials for various crimes. DHS then runs the names of these individuals through its records to see if they are in the U.S. unlawfully or otherwise subject to deportation.[45]
At this point, however, DHS begins to twist the law. If the individual is known to be in the U.S. illegally, ICE officers must go to the local jail and interview the individual in order to determine whether to pursue immigration charges. If an individual found through Secure Communities did not meet the Administration’s enforcement priorities, he was simply allowed to remain in the United States. Essentially, all that local governments do is hold the individual for a few days and provide fingerprint information to the FBI as they normally would.[46] In April 2012, however, ICE announced that it would no longer ask local jails to detain unlawful immigrants who were stopped for “minor traffic offenses” and other lesser offenses, reducing Secure Communities’ effectiveness.[47] Bizarrely, ICE also stated that it would analyze and take steps against local jurisdictions where arrest-rate data was “abnormal,” hinting at the idea that DHS would go after communities where the arrest rate of illegal aliens was too high, despite DHS’s constant claims of limited resources.[48] Finally, in President Obama’s executive actions in the fall of 2014, Secure Communities was formally discontinued, with ICE starting a new program that will have an even more limited scope. This program, called the Priority Enforcement Program (PEP), will cease to enforce any immigration offenses unless the individual is already a convicted criminal.[49]
Even as the Secure Communities program has been removed as an immigration enforcement tool, the 287(g) program has been openly assaulted by the Obama Administration because it allows local and state officials to enforce U.S. immigration law. Local law enforcement officers must undertake training and enter into memorandums of agreement with ICE to receive immigration-law-enforcement authority; 287(g) officers are then authorized to arrest individuals and begin the removal process, essentially acting as an extension of ICE. This program is cost-effective at approximately $68 million a year, and acts as a force multiplier for ICE.[50] But enforcing U.S. immigration laws against most illegal immigrants is exactly the opposite of DHS’s stated immigration priorities. As a result, 287(g) has come under consistent attack from amnesty activists and the Obama Administration. President Obama’s budget proposal has twice recommended steep cuts in 287(g), most notably for FY 2014 when the President’s budget would have slashed $44 million, almost two-thirds of the 287(g) program’s budget.[51]
At the same time, the Obama Administration has sought to tie the hands of local governments by limiting how they enforce the law, or by simply ignoring or rescinding 287(g) agreements. In December 2011, DHS rescinded Arizona’s Maricopa County’s 287(g) agreement and restricted access to the Secure Communities program.[52] Then, in June 2012, immediately following the Supreme Court’s decision to uphold most of Arizona’s immigration law, DHS rescinded all of its street-level 287(g) agreements in Arizona.[53] Since allowing local law enforcement officers to enforce the law is against DHS’s Administration-mandated objectives, President Obama has used every tool to assault the 287(g) program to ensure that immigration laws are not enforced.
If the U.S. is to enforce its immigration law, states must be a part of the solution. Any Administration can and should expand 287(g) agreements and call on the assistance of state governments through other cooperative immigration-law-enforcement programs. Furthermore, rather than suing states for correctly enforcing the letter and intent of federal immigration laws, this and future Administrations should cooperate with and support state governments, and only take action against those states that are breaking immigration laws—such as by providing in-state tuition to illegal immigrants. At some point, Congress can follow up and expand cooperative programs by requiring DHS to accept requests from state and local governments to enter into a 287(g) agreement. Congress should also forbid DHS from providing grant money to cities that resist the enforcement of immigration law, known as sanctuary cities. While federalism gives local governments some latitude in choosing to oppose or not assist the federal government in enforcing immigration law, the federal government does not have to reward or pay for the results of such policies.
In addition to ERO, ICE’s HSI office also conducts important work, though its missions are more in the vein of traditional law enforcement. In addition to various police, national security, and intelligence functions, ERO plays a unique role in the vetting of visa applications through the Visa Security Program (VSP) in HSI’s international operations division. The VSP deploys HSI agents to critical embassies and consulates around the world to advise and assist State Department officials in the visa-adjudication process. HSI officers bring law enforcement and security expertise to high-risk diplomatic posts, and work with local law enforcement to further improve detection of potential threats stemming from that country. To this end, ICE had deployed about 250 special agents, as well 170 support staff to 62 offices throughout 26 countries in 2015. The VSP reviewed over two million visa applications, including 8,600 visa refusals, of which 2,200 were for suspected terrorist connections or activity.[54] The VSP program also participates in the Security Advisory Opinions (SAO) program, which provides additional scrutiny to high-risk applications. The PreAdjudicated Threat Recognition Intelligence Operations Team (PATRIOT) is a related program that brings together CBP, ICE, Intelligence Community, and State Department officials to investigate suspicious visa applications. Making HSI resources and officers available to State Department visa officials should be expanded to improve vetting.
Actions for Congress. Ultimately, major changes in policy are required to fix ICE and the U.S. immigration system. ICE will also need greater funding to allow it to remove more illegal immigrants and ensure that those who remain in the country show up at their court hearings. Additional funding will also collapse the Obama Administration’s claim that ICE is held back only by finite resources. Congress should:
- Defund the President’s executive actions on immigration enforcement. The Obama Administration has issued a series of policy memorandums that do not allow ICE ERO officers to do their jobs. To improve morale and enforce existing immigration laws, Congress should prohibit any funding in support of these amnesty and non-enforcement policies. Failing to do so jeopardizes Congress’s constitutional authority and sets a dangerous precedent that empowers the executive branch in ways that all Americans should fear.
- Strengthen the 287(g) program. Designed to make it easier for state and local governments to assist in enforcing federal immigration laws, 287(g) has been under assault during the Obama Administration, which has sought to cut funding, access to, and use of, the program. Congress should widen 287(g) usage by increasing funding for the program and requiring DHS to enter into a 287(g) agreement with any state and local government that requests entry, with significant consequences should DHS not meet this requirement in a timely fashion.
- Increase rapid-removal authority. Currently, Administration policy restricts ICE from removing many illegal immigrants in an expedited manner. To prevent future humanitarian and security crises on the border, ICE should be allowed to rapidly remove any illegal border crosser. This can be accomplished by making this authority explicit in section 235 of the Immigration and Nationality Act and by reforming the William Wilberforce Trafficking Victims Protection Reauthorization Act of 2008 to clarify that children who are not victims of human trafficking should also be removed in an expedited manner to discourage future surges.
- Provide more prosecutors and agents. In addition to letting ICE agents do their jobs by removing non-enforcement policies, Congress should increase the number of ERO officers as well as a corresponding number of prosecutors and legal personnel to be able to expedite necessary removals. Additional agents for HSI will also allow the U.S. to expand the VSP to improve visa vetting.
- Increase the number of illegal immigrants who appear at their court hearings. While more detention beds guarantees that more individuals will show up to immigration proceedings, this system can be expensive. Increasing the use of the most effective ATD, such as GPS tracking anklets, in addition to detention facilities, is a cost-effective way of reducing the number of absconders.
To fund these activities, the Heritage budget recommends $7 billion for ICE.
Additionally, Heritage recommends that Congress provide the Justice Department with additional funds for immigration court judges to support the work of increased ICE operations.
5. Transportation Security Administration
The President’s FY 2017 budget requested $7.59 billion for the TSA, slightly more than the FY 2016 appropriation of $7.44 billion in total budget authority. Perhaps the DHS component most recognized by the general public, the TSA was created after 9/11 to protect U.S. transportation systems, including trains and buses, though aviation security is its prime focus.
The TSA could benefit from significant changes and reforms. Continuing to expand and strengthen trusted-traveler programs, such as PreCheck, will increase the time that TSA screeners spend on travelers of higher or unknown risk. The TSA should also be forced to expand the Screening Partnership Program (SPP) that saves the government money and enhances productivity by allowing airports to use private screeners (with TSA oversight) in place of TSA screeners. Additionally, Congress should rethink the 100 percent screening of air cargo and provide more financial support to the Federal Flight Deck Officer (FFDO) program as a cost-effective supplement to the Federal Air Marshal Service (FAMS).
DHS has several trusted-traveler programs that give participating low-risk travelers access to streamlined security, customs, and immigration screening. These programs, including TSA PreCheck and CBP’s Global Entry, NEXUS, and SENTRI, are all predicated on the concept of risk-based security. The U.S. could treat every individual who enters the U.S. as an equal potential threat to U.S. security, or it could differentiate between lower-risk individuals and those who present greater risks, or whose risk is simply unknown. This risk-based security allows the U.S. to use its limited security resources more efficiently.
TSA PreCheck generally ensures that participants receive an expedited screening process, including the ability to keep on shoes, belts, and light jackets, and to keep computers and liquids in their bags at roughly 160 participating airports and with 16 airlines.[55] To join PreCheck, individuals must apply in person at a TSA application center and undergo a background check, be enrolled in one of the other trusted traveler programs, or be a member of the military or a military academy. Additionally, PreCheck occasionally includes frequent travelers as well as unvetted individuals through a process known as “managed inclusion,” which allows a number of random travelers to use the PreCheck line.[56] TSA PreCheck enrollment grew from around 4,000 travelers in December 2013 to 2 million in January 2016.[57] However, to make TSA PreCheck an efficient use of resources and effective at speeding up security lines, the TSA needs to further expand enrollment in the program.
While the TSA is continuing to expand PreCheck, concerns regarding security have been raised by the IG, the GAO, and independent researchers, especially after a serious criminal was able to pass through a PreCheck line after a faulty risk assessment declared him to be low risk.[58] As a result, the new TSA Administrator, Peter Neffenger, has ordered that managed inclusion be phased out with one part cancelled in late 2015.[59] Additional security assessments should be undertaken and heeded if PreCheck is to remain a beneficial tool to the TSA. Much of these assessments will have to be classified, but Members of Congress should be informed, and unclassified findings should be made available when possible. Congress should address these classified findings regarding how it can mitigate risks in the PreCheck system.
The TSA also manages the screening of travelers and cargo. Unlike TSA PreCheck, a security policy that needs to be rethought is the 100 percent screening of air cargo. The TSA currently screens 100 percent of all domestic air cargo at levels “commensurate with screening of passenger checked baggage,” as required by the Implementing Recommendations of the 9/11 Commission Act.[60] The language of the act, however, was very broad and seemed to include international cargo, and the TSA is currently screening 100 percent of high-risk cargo, since complete screening at a hundred or more international airports would be extremely problematic from logistical and diplomatic perspectives. With the growth of capabilities, such as CBP’s Automated Targeting System, that determine the risk level of cargo by checking manifest and cargo data against a variety of intelligence databases, examining the nature of the cargo, its source, its destination, and other factors, the TSA should move from the costly and disruptive 100 percent scanning mandate to a risk-based approach. This approach would use risk factors and intelligence to determine which pieces of cargo deserve closer inspection, rather than treating all cargo as carrying the same risk.[61] At the very least, the TSA should make it easier for companies to comply with the mandate, such as through the Certified Cargo Screening Program (CCSP), which would lessen costs and make cargo transportation easier and faster.[62]
Famously, the TSA also scans passengers before boarding a flight—with poor results. John Roth, the DHS IG, stated in early 2015 that he was “deeply concerned” about the TSA’s inability to protect travelers, noting that the TSA has received over 100 warnings for its shortfalls.[63] He testified recently that:
We have conducted a series of covert penetration tests—essentially testing TSA’s ability to stop us from bringing simulated explosives and weapons through checkpoints, as well as testing whether we could enter secured areas through other means. Although the results of those tests are classified, we identified vulnerabilities caused by human and technology-based failures.
We have audited and reported on TSA’s acquisitions. Our audit results show that TSA faces significant challenges in contracting for goods and services. Despite spending billions on aviation security technology, our testing of certain systems has revealed no resulting improvement.
We have examined the performance of TSA’s workforce, which is largely a function of who is hired and how they are trained and managed. Our audits have repeatedly found that human error—often a simple failure to follow protocol—poses significant vulnerabilities.
We have looked at how TSA plans for, buys, deploys, and maintains its equipment and have found challenges at every step in the process. These weaknesses have a real and negative impact on transportation security as well.[64]
The IG also found that the TSA’s efforts to vet airline workers have not been entirely successful. In a recent review of airline workers, 73 were found to be part of the larger Terrorist Identities Datamart Environment (TIDE), the government’s most comprehensive database on known and suspected terrorists. While these individuals were not part of the higher-risk Terrorist Screening Database, it is highly concerning that 73 airport employees may have links to terrorist activity.[65] The TSA has requested that it receive expanded access to additional parts of the TIDE.
Perhaps most worryingly, the TSA failed to stop weapons and bomb materials smuggled by undercover agents in 67 of 70 recent probes of airport security across the country. While Homeland Security Secretary Jeh Johnson announced that changes were being made,[66] and a new administrator has taken over, this dismal record calls into question the entire reason for the TSA’s existence. Such undercover “red team” exercises should be expanded and become a key metric for determining the success of airport security.
Such failures highlight the fact that the federal government and the TSA need not conduct frontline screening, as there is an effective and less costly alternative in the Screening Partnership Program (SPP) that substitutes private screeners with TSA oversight in place of TSA screeners. Created as a result of the Aviation and Transportation Security Act of 2001, the SPP allows airports to opt out of federal screening so long as they can show that private screening will not cost more, compromise security, or harm the effectiveness of screening.[67]
Despite its potential benefits and the TSA’s current challenges, the SPP has had a rocky implementation, being suspended by the Obama Administration before Congress restored it.[68] As of January 2015, 21 airports were participating in the SPP.[69] There are multiple reasons why an increasing number of U.S. airports are using the SPP, including productivity, cost, and security. In terms of productivity, a case study by the House Transportation and Infrastructure Committee in 2011 found that SPP screening was as much as 65 percent more efficient than federal screening.[70] One reason for this productivity gap could be the higher level of attrition in the TSA than in private screening companies. A related factor in productivity could be better staffing measures, ranging from day-to-day scheduling to more efficient hiring and union practices. Beyond pure efficiency, SPP airports also report improved customer service.
Productivity also bleeds over into considerations of cost, since a more productive workforce with less attrition is less expensive to maintain and operate. Although TSA studies found SPP programs to be more costly than government screening, these studies were widely criticized, including by the GAO, for flawed methodologies. When some of these flaws were corrected, the TSA found SPP and government screening to be nearly equal in cost.[71] Furthermore, the House Transportation and Infrastructure Committee study found that when considerations, such as increases in productivity were accounted for, the cost of the program fell dramatically. Together with smaller overhead costs and lower levels of attrition, the SPP is likely a financial boon for most airports.
Nearly every study undertaken, whether by the TSA or other organizations, has found that private screeners, while no silver bullet solution, are at least as good as, if not better than, government screeners at detecting security threats.[72] It is also worth considering that, if a private contractor fails to provide adequate security, perhaps by failing a red team test, the contractor can be replaced. The same cannot be said of the TSA.
It is for all these reasons that the vast majority of European countries allow airports to provide their own screening force or hire a contractor to provide it.[73] Unfortunately, the process for joining and renewing an SPP contract remains mired in bureaucracy, taking as long as four years.[74] In the U.S., rather than allowing an airport to determine the best way to provide screening, the SPP is micromanaged by the TSA, with the TSA selecting a screening contractor for each SPP airport. Furthermore, the TSA has given its workforce collective bargaining rights, pitting security and cost-effectiveness against labor demands.[75]
Finally, the TSA is also responsible for last lines of defense in aviation security—the Federal Air Marshals and Federal Flight Deck Officers. While FAMs, highly trained agents who fly aboard some aircrafts, are relatively well known and provide an additional layer of security to some flights, FFDOs are much less well known. FFDOs are pilots or navigators who have been trained by the TSA to use firearms to stop a hijacking. FFDOs voluntarily join the program and must pay for a great deal of the costs of the FFDO program themselves, with estimates running as high as $10,000.[76] The TSA is currently covering the cost of the training itself, as well as meals and lodging at federal law enforcement training centers, but not transportation or time off from work.[77] The result is that the cost of the FFDO program is estimated at a mere $20 per flight, as opposed to the cost of a FAM of around $3,000.[78] Expanding funding for the program could help train additional FFDOs and help cover some of the personal costs involved in becoming an FFDO.
Actions for Congress. To improve transportation security, Congress should:
- Improve security assessments. In order to ensure security and continue the growth of TSA PreCheck and risk-based security, the TSA must conduct proper security assessments and refine the screening and vetting process to minimize security risks. Red team and other covert exercises and testing should become a larger part of these assessments as such tests are an effective way to judge the success of airport security.
- Embrace risk-based screening and security. Efforts such as the Automated Targeting System, which would subject cargo to a risk rating that determines whether it should be given additional screening, are the way to improve air cargo security. Congress and DHS should look for ways to move away from a blanket screening process. At a bare minimum, they should expand the Certified Cargo Security Program, which allows the private sector to more easily meet the 100 percent screening mandate. Congress and the TSA should also look to expand enrollment in TSA PreCheck to shorten airport security lines.
- Simplify the SPP approval and contracting process. The process for joining SPP should be streamlined to make it easier for airports to apply, and to make TSA adjudication and processing faster, fairer, and more consistent. Airports joining the SPP should also be allowed to select and manage their own screening contractors from a list of TSA-approved companies, instead of continuing the TSA’s micromanagement of the program.
- Limit collective bargaining. Collective bargaining in the screening line is harming security and costing taxpayers and travelers. Congress should expressly forbid the TSA from bargaining collectively.
- Expand the FFDO program. Greater funding for FFDO will enable this extremely cost-effective program to expand significantly.
- Review alignment of the TSA budget with the risks. TSA resources for any given activity should match the relative level of risk that that activity is working to mitigate. This requires the TSA, its IG, or the GAO to examine classified risk assessments and realign funding to better match the severity of different risks.
To fund these activities, the Heritage budget recommends $7.5 billion for the TSA.
6. Coast Guard
With a budget of approximately $11.1 billion in FY 2016 (President Obama requested $10.3 billion for FY 2017), the Coast Guard is a unique part of DHS: It is the only military branch that is not a part of the Department of Defense. It has a variety of missions, including interdiction of narcotics and other illicit trafficking, search and rescue, maintaining safety and security in the Arctic, and providing port security. With such a wide range of missions, the need for meeting Coast Guard modernization goals is great. Unstable and underfunded budgets have strained the Coast Guard’s operational availability in recent years. This is particularly the case with a few major vessel programs, such as the Offshore Patrol Cutter (OPC) and the Fast Response Cutter (FRC). Congress should ensure that the Coast Guard has the resources it needs to protect U.S. waters and provide for the common defense. Without funding the Acquisition, Construction, and Improvements (AC&I) budget at the minimum level that the Coast Guard says is necessary—$1.5 billion—it will continue to fall behind in recapitalizing the fleet.
Critical Platform Funding Reforms. Critical platform funding reforms are needed for the OPC, the FRC, unmanned aerial systems (UASs), and polar icebreakers.
Offshore Patrol Cutter. According to Coast Guard Commandant Admiral Paul F. Zukunft, the OPC is the Coast Guard’s “number one acquisition priority.”[79] The Coast Guard’s program of record (POR) states that 25 OPCs are necessary to replace the service’s 29 medium-endurance cutters (WMECs).[80] However, continued irregularities and delays in the program’s funding cycle have pushed back initial procurement from 2016 to 2018—meaning that they will not be operational until at least 2021.[81] It is therefore crucial that the Coast Guard strive to begin replacing the legacy craft in this cutter class, some of which are more than 50 years old. Furthermore, alternative analyses of the Coast Guard’s capacity suggested that between 32 and 57 OPCs are necessary to meet mission while accepting different levels of risk.[82] This year’s budget proposal takes a step in the right direction for OPC, requesting $100 million to begin purchasing long-lead-time material, and continued review of progress and design details. Congress should ensure that this is sufficient to begin procuring OPCs by FY 2018.
Fast Response Cutter. Though the Fast Response Cutter is being produced at a high rate, the Obama Administration continues to underfund this program in order to pay for other priorities. As Coast Guard officials have mentioned in the past, the FRC program should continue to procure six vessels per year to both replace legacy craft and to yield better economies of scale.[83] In FY 2017, the Coast Guard requested funding only for four—$240 million instead of the $325 million that had been previously proposed. This is interesting because the value of two FRCs (roughly $108 million) is near the amount requested this fiscal year for the polar icebreaker program ($150 million), indicating that there is an unofficial ceiling imposed on the Coast Guard AC&I budget despite commandants consistently calling for an increase to it. Because the icebreaker has become a larger priority by nature of President Obama’s order to accelerate its production, the FRC request was possibly cut to make this happen. The Coast Guard should not have to make short-sighted sacrifices elsewhere in its AC&I budget to pay for the icebreaker.
Unmanned Aerial Systems. The Coast Guard would also benefit greatly from procuring UASs to support NSC operations. According to the GAO, “Coast Guard officials acknowledged that the lack of [cutter-based] unmanned aircraft would create a gap between the NSC’s actual and planned capabilities.”[84] Dr. William Posage, program manager for the Coast Guard Research and Development Center, explained that the lack of cutter-based UAS technologies “left the NSC with an enormous surveillance gap in her ability to perform her mission.”[85] Notably, the operational effectiveness of the NSC without a UAS component would “be comparable to that of the 378-foot Hamilton class high-endurance cutter,” the very program it was designed to replace with capability enhancements.[86]
The Coast Guard has successfully tested the FireScout and ScanEagle UAS platforms, both of which would significantly amplify the NSC’s surveillance, detection, classification, and prosecution capabilities. Widely used for similar naval operations, they have successfully contributed to a handful of at-sea Coast Guard demonstrations. According to an assessment by the Coast Guard Office of Aviation Forces, the presence of two vertical take-off FireScout UASs aboard an NSC would enable the cutter to cover three times the presence radius of an NSC without them.[87] Similarly, according to a Senate Appropriations Committee report, “[t]he Coast Guard has reported…that its long standing plan to add vertical take-off unmanned aircraft systems to the National Security Cutters would result in an estimated 95- to 225-percent increase in surveillance coverage within an 800 nautical mile radius of the cutter and an estimated 95-percent increase in the number of prosecutions achieved by the cutter.”[88]
The Coast Guard’s FY 2017 budget justification states that funding for the NSC program will in part “establish sUAS [small UAS] capability aboard one NSC, to include engineering analysis, non-recurring engineering, procurement and installation of sUAS components, and system testing and certification.”[89] Admiral Zukunft testified before the House Transportation Committee in March 2016 that this activity would involve a “down select” for a sUAS capability “that will go on board” the NSC.[90] The NSC will amplify its aerial ISR capabilities dramatically with the longer-term integration of sUAS, while the sea service should continue to evaluate the vertical unmanned aerial vehicle (VUAV) platform.
Polar Icebreakers. The Coast Guard requires at least three heavy and three medium polar icebreakers to fulfill its polar missions.[91] Currently, it only operates one of each.[92] Given increasing economic, safety, and security interests in the Arctic, the need for icebreaking capacity will only increase in the future. President Obama announced during his trip to Alaska in 2015 that he is directing the government to accelerate procurement of one heavy polar icebreaker from FY 2022 to FY 2020.[93] Rough estimates have found that one heavy polar icebreaker built in the U.S. would cost around $1 billion.[94]
This year, the Coast Guard requested $150 million for the heavy polar icebreaker, much higher than amounts in previous years, partly driven by the President’s direction to accelerate it. While this displays a more legitimate commitment to fielding this capability, the government should make sure that it looks at all options to build it. This should include foreign shipbuilding companies, some of which have had consistent experience building such vessels and therefore purportedly can construct icebreakers at much lower cost than can the U.S.[95]
As mentioned, there appears to be a ceiling for overall acquisition funding imposed upon the Coast Guard, possibly by DHS or the Office of Management and Budget. The Coast Guard has repeatedly stated that a minimum of $1.5 billion (and upwards of $2.5 billion) for AC&I is necessary to continue to recapitalize the fleet at an acceptable rate.
The program of record itself accepts a significant amount of risk with which Congress may not be comfortable. If Congress does not want to accept that much risk, it will need to revisit the alternative fleet mix analyses, that is, fleet sizes larger than the current program of record that the Coast Guard has studied. Congress will then need to work with the Coast Guard to determine how additional funding for ships and platforms can best reduce risk, and provide the necessary funding level accordingly. Since the Heritage DHS budget is finding significant savings elsewhere, there is room for more funding should the Coast Guard and Congress believe that it requires a fleet size beyond that of the current program of record.
Actions for Congress. To improve USCG effectiveness, Congress should:
Recapitalize the Coast Guard. Funding for acquiring new Coast Guard vessels has been regularly short of what is necessary to complete the Coast Guard’s mission, and often results in additional acquisitions inefficiencies and costs. Congress should commit to providing the Coast Guard with consistent acquisitions funding so that the USCG will have the vessels it needs to complete its missions. Congress should also ensure that any additional resources it provides to the Coast Guard are used to meet important priorities, including cost-efficient acquisition of the FRC, OPC, and unmanned systems.
To fund these activities, the Heritage budget recommends $10.85 billion for the USCG:
- A minimum of $1.5 billion for AC&I. This funding should include six FRCs, a clearer path to fielding OPCs more rapidly, a cost-effective icebreaker program for meeting icebreaking requirements, and robust investments in aviation assets, particularly unmanned systems.
- $7.06 billion for operating expenses. FY 2016 appropriations included $7.06 billion for operating expenses, including $160 million for Overseas Contingency Operations. The Heritage budget maintains this level of OCO funding for 2017.
- The USCG should maintain funding for other programs. Environmental compliance, reserve training, health care, retirement pay, and other programs are funded at levels requested by the President.
7. U.S. Secret Service
The U.S. Secret Service’s total funding fell slightly in the President’s FY 2017 budget (to $2.16 billion) from FY 2016’s level of almost $2.2 billion. The USSS is well known for its protective mission, but it is also responsible for combatting currency counterfeiting and other financial crimes. Its protective mission currently faces numerous challenges, springing from multiple high-profile security failures in the past several years. While the Secret Service has had three different directors over the past three years, embarrassing incidents continue. Despite a review commission in the fall of 2014 and ongoing bipartisan scrutiny in Congress, the Secret Service seems to continue to slip, requiring more substantial changes and reforms to restore the Secret Service to the level of excellence for which it has typically been known.
A short chronology of the Secret Service’s recent failures includes:
- November 2009. Husband and wife Tareq and Michaele Salahi attended a state dinner at the White House and met with President Obama—despite the fact that they were not on the guest list.[96]
- November 2011. A man with a semi-automatic rifle fired at the White House, with at least seven bullets hitting the building. While Secret Service agents initially rushed to respond with weapons drawn, they were told to stand down by their supervisors—who attributed the shooting sounds to backfiring vehicles. Some agents dispute this account while others remain silent “for fear of being criticized.”[97] At the time, the President’s daughter Sasha was at home, and his other daughter Malia was expected home soon. Despite the fact that the shooter’s vehicle and gun were found within 10 minutes, an investigation was not initiated until a housekeeper noticed broken glass and bullet holes four days later.[98]
- April 2012. Secret Service agents who were a part of President Obama’s advance team to Cartagena, Colombia, engaged in sexual conduct with prostitutes.[99]
- May 2013. A Secret Service supervisor removed ammunition from his gun and left a bullet in a woman’s room at the Hay-Adams Hotel across the street from the White House and allegedly tried to force his way back into the room to retrieve it. Further investigation reveals that this same supervisor and another Secret Service official sent sexual e-mails to a female subordinate, resulting in their suspension.[100]
- March 2014. Three Secret Service agents in Amsterdam were disciplined after a night of heavy drinking that left one agent passed out in a hotel hallway just one day before President Obama arrived.[101]
- September 2014. The Secret Service was unaware that an armed security contractor with a criminal record was on the same elevator as President Obama during a trip to Atlanta.[102] Several days later, a fence jumper managed to run into the inner rooms of the White House before being taken down by an off-duty agent. Reportedly, the alarm system was turned off because it bothered White House staffers.[103]
- October 2014. New information surfaced about the 2012 prostitution scandal involving Secret Service agents in Colombia indicating that White House aides knew about the involvement with prostitutes but did not investigate, and possibly interfered with other investigations.[104]
- March 2015. Two senior Secret Service agents drove a government vehicle into the barricades outside the White House on March 4. The agents, including Marc Connolly who was the second-most senior agent on President Obama’s security detail, appeared to be drunk and according to news reports, had just come from a party where alcohol was consumed.[105] Rather than arrest the officers and conduct sobriety tests, however, the supervisor on duty ordered that the agents—Connolly and George Ogilvie—be sent home. An investigation into the incident has concluded that “it was more likely than not that Connolly and Ogilvie’s judgment was impaired by alcohol,”[106] resulting in Connolly’s resignation.[107] Then on March 31, a manager in the Secret Services security clearance division was accused of sexually assaulting a female employee after returning to the office with her after a party. The manager is currently being investigated by the IG and Washington, DC’s sex crimes unit.[108]
- April 2015. A Secret Service officer was charged with first-degree attempted burglary and destruction of property stemming from a domestic dispute with the officer’s ex-girlfriend.[109] In a separate incident, following a congressional hearing on Secret Service failures led by Chairman Jason Chaffetz, Chaffetz’s application to the Secret Service was accessed about 60 times in March and April 2015 in contravention of privacy laws, and information in it was shared with others, including at least one person outside the Secret Service.[110]
With this record of embarrassing security incidents and the underlying problems that are creating them, morale at the Secret Service has plummeted, possibly to an all-time low. In the Partnership for Public Service’s 2011 survey of the Best Places to Work in the Federal Government, the Secret Service was considered an above-average place to work. Steadily declining since then, in the 2015 survey, it plummeted to 2nd-worst agency for which to work in the federal government.[111]
As these incidents began to pile up, Homeland Security Secretary Johnson ordered a review of the Secret Service. A review panel found three major problem areas:
- Training and personnel;
- Technology, perimeter security, and operations; and
- Leadership.[112]
The panel found that the amount of on-the-job training for both the Presidential Protective Detail (PPD), and the Uniform Division that protects the White House and other sites, have “fallen below acceptable levels.”[113] The panel also found that there were too few agents and officers to both meet mission needs and have time for training. The review panel and the Secret Service are unable, however, to appropriately size its force since the relevant data are not available. The review panel recommended increasing the number of agents and officers by about 285, but noted that this would be just the first step toward right-sizing the service. The panel also found that the White House fence was not tall enough nor designed appropriately to hinder or stop potential intruders, a problem at least partially addressed by the addition of spikes to the fence in the summer of 2015.[114]
But the most important finding of the panel was that “[f]rom agents to officers to supervisors, we heard a common desire: More resources would help, but what we really need is leadership.” The review panel believed that leadership and accountability by the director of the Secret Service to every agent is the priority. To this end, the panel recommended that the next Secret Service director come from outside the service, to ensure that an “honest top-to-bottom reassessment” of the service could be completed.[115] The review panel found that increased interaction with relevant experts outside the Secret Service and improved administrative capabilities would help to improve efficiency and effectiveness. Particularly, accountability must be re-instilled in the management ethos of the service since “accountability creates the culture of performance that the Secret Service needs to meet its zero-failure mission.”[116]
Despite the recommendation for a director from outside the service, President Obama chose the former head of the PPD, Joseph Clancy, as the new director. This does not mean that the Secret Service cannot be fixed under Director Clancy, who certainly has the experience and expertise to do so, but that the level of true soul-searching and complete reassessment of the agency may be more difficult. That said, it is too early to know if Director Clancy is taking the right steps.
Actions for Congress. To support the reform of the U.S. Secret Service, Congress should:
- Increase Secret Service staffing. The review panel recommended 85 more PPD agents and 200 more officers, but called on the service to create a mission-based budget that will determine the appropriate staffing levels.
- Mandate increased training. The panel called for PPD agents to spend 25 percent of their on-duty time in training, the so-called Fourth Shift. For the officers, a minimum of 10 percent on-duty training time should be required.
- Require increased disciplinary and accountability standards. When improper behavior or mistakes are made, the Secret Service should demand a strict disciplinary or corrective action. Supervisors and managers must be made to uphold these standards or be held accountable themselves. Congress should require the GAO to report on how these standards are employed and whether they are instilling discipline across the service.
- Expand the number of professional administrators, rather than agents or officers, responsible for budgeting and workforce functions. The review panel points out that agents and officers may not always be the best at completing administrative tasks, and that a larger suite of professional administrators could support and improve planning and execution of core responsibilities.
- Provide continued oversight to ensure that reforms are completed thoroughly.
To fund these activities, the Heritage budget recommends $2.2 billion for the USSS.
8. National Protection and Program Directorate
The National Protection and Program Directorate (NPPD) received approximately $3.08 billion in FY 2016, and President Obama’s FY 2017 request calls for a slight decrease, to $3.04 billion, though this decrease is largely explained by a request to transfer the Office of Biometric Identity Management from the NPPD to CBP. The NPPD is the primary component of DHS that is responsible for cybersecurity and the protection of critical and government infrastructure. While the NPPD has this responsibility, the vast majority of critical infrastructure (generally estimated at more than 90 percent) is owned and operated by the private sector.[117] As a result, the NPPD, whether it is working in cyberspace or securing a chemical facility, often supports, collaborates with, or regulates private-sector efforts. The NPPD also protects federal facilities, both in cyberspace and physical locations, and manages DHS’s primary biometrics database, IDENT.
Cybersecurity. The NPPD is the primary hub for cybersecurity, not only for DHS, but for all civilian government agencies. Within the NPPD, the Office of Cybersecurity and Communications (CS&C) is the primary office managing cyber operations, with support from the Office of Cyber and Infrastructure Analysis. CS&C is tasked with leading the effort “to protect the federal ‘.gov’ domain of civilian government networks,” and also works with the private sector to protect critical infrastructure and businesses. Much work remains to be done in this area, both in DHS and across the federal government, as a recent study found that government cybersecurity rated worst in a study of 18 major industries.[118]
Within CS&C, the primary hub of cybersecurity operations is the National Cybersecurity and Communications Integration Center (NCCIC). The NCCIC is “a 24x7 cyber situational awareness, incident response, and management center that is a national nexus of cyber and communications integration for the Federal Government, intelligence community, and law enforcement.”[119] The National Cybersecurity Protection Act of 2014 formally made the NCCIC a hub for sharing and receiving information from the private and public sectors, improving awareness and preparedness for cyber vulnerabilities, threats, and mitigation options. With the passage of the Cybersecurity Information Sharing Act (CISA), which provides additional protections for those that share information, and additional procedures for that sharing and spread of information, the NCCIC will assume an even more central role in sharing cyber information with others in government and the private sector.[120] In addition to sharing information on cyber threats and vulnerabilities, the NCCIC also contains the United States Computer Emergency Readiness Team (US-CERT) and the Industrial Control Systems Cyber Emergency Response Team (ICS-CERT). As their names imply, these organizations specialize in responding to major cyber incidents in order to stop or mitigate a breach or an attack; both CERTS also work to prevent cyber incidents by sharing cybersecurity information with public-sector and private-sector partners.
CS&C also has two offices—(1) Federal Network Resilience and (2) Network Security Deployment—focused on defending federal networks, as DHS was charged in 2010 with overseeing the cybersecurity of federal civilian agencies. To this end, CS&C runs multiple programs including the National Cybersecurity Protection System, more commonly known as the Einstein family of systems. Einstein 1 focused on passively collecting information on network traffic of government organizations. Einstein use corresponded with the implementation of the Trusted Internet Connection (TIC) initiative in the mid- and late 2000s, which sought to have data flowing into government networks through 50 separate Internet gateways, a measure that makes it easier for the government to monitor data flowing to and from government computer networks and stop malicious behavior.[121] Einstein 2 built on these capabilities by detecting intrusions and malicious computer network activity that came through the TICs. Einstein 3 Accelerated (E3A) is now being implemented; it is intended to prevent and disrupt intrusions into federal networks by using threat and vulnerability signatures to find malicious behavior.[122]
A recent GAO report, however, indicated that Einstein faces multiple difficulties. The GAO found that Einstein was unable to detect a worryingly large number of potential threats and vulnerabilities. For example, for five applications (Adobe Acrobat, Flash, Internet Explorer, Java, and Microsoft office), only 6 percent of known vulnerabilities were covered by Einstein.[123] The GAO found that Einstein was not drawing on important sources of vulnerability information, such as the National Vulnerability Database (NVD) held by the National Institute of Standards and Technology (NIST) or DHS’s Continuous Diagnostics and Mitigation (CDM) program that detects vulnerabilities in federal systems, such as poor passwords or unpatched systems.[124] DHS said that it is working to incorporate additional sources into its databases, and noted that Einstein should not be the only security system a department uses.
Beyond difficulties with vulnerability and threat signatures, the GAO also found that Einstein was enabled at only five of the 23 customer departments, and even among those five some types of Web communications, such as e-mail, were not being monitored. Much of this difficulty lies in the dual responsibility for cybersecurity that lies with DHS and each department. While DHS’s cyber programs can provide some level of security for .gov domains, each department is responsible for much of its own cyber activity, including how well it uses programs like Einstein. The GAO recommended that DHS provide better guidance to other departments on how to ensure that online traffic is routed through Einstein sensors.
Additionally, Einstein is only a signature-based system that does not use anomaly-based or stateful-purpose detection methodologies, which are more complex approaches that “involve comparing current network activity to predefined baselines of ‘normal behavior’ to identify deviations that could be indicative of malicious activity.” These approaches to intrusion detection are more effective than signature-based detection in identifying previously unknown threats, such as “zero-days” or attacks that have no patch or fix.[125] DHS stated that it is piloting new technologies to detect anomalous network activity and build upon Einstein.
CS&C also runs the Enhanced Cybersecurity Services (ECS) program in order to improve the cybersecurity of owners and operators of critical infrastructure.[126] ECS does so by providing classified and sensitive cyber threat information to approved commercial service providers—currently AT&T, Verizon, and CenturyLink—that can provide better security services to critical infrastructure.
For quicker automated sharing of threat data among and between the private and public sectors, CS&C is working with the MITRE Corporation on the STIX and TAXII systems. STIX is essentially a common language that can be used to detail threats,[127] while TAXII enables automatic sharing of data in the STIX format.[128] The goal of STIX and TAXII is to make information sharing as quick and helpful as possible, with the added privacy advantage of minimizing personal information and focusing sharing on the coding of threats and threat actors.
DHS is also responsible for the Critical Infrastructure Cyber Community (C3) Voluntary Program, which promotes the adoption of the National Institute of Standards and Technology’s (NIST) Cybersecurity Framework.[129] Created by Executive Order 13636, the framework designed by NIST and supported by DHS is primarily built around a voluntary set of cybersecurity standards and best practices.[130] These standards were created by NIST; DHS’s role is to encourage their adoption generally, while sector-specific agencies, such as the Department of Energy, may use existing regulatory authority to apply the standards to the energy sector.[131]
Though the NPPD operates these and other cybersecurity programs, it has not done so without challenges. As with many other DHS organizations, the NPPD as a whole must deal with the crippling problem of poor workplace satisfaction. In the 2015 Best Places to Work in the Federal Government, the NPPD rated 312 of 320 subcomponents. While relatively low pay at higher levels may be an issue, especially in the cyber field, the NPPD employees complained mainly about the lack of leadership, training, and performance-based rewards. Indeed, in October 2013, the DHS IG also found that, due to a lack of funding, the training of employees at the NCCIC was not providing NCCIC personnel with the specialized training they needed.[132] Together with bureaucratic hiring processes, the NPPD has trouble finding and keeping trained and talented cybersecurity professionals, especially at more senior levels.[133] Congress tried to ease this problem by passing a cyber workforce measure that made pay more competitive for cyber positions, and called for a strategy to identify, hire, and keep skilled experts.[134] Communication with the NCCIC seems to indicate that DHS has made progress in the past few years in building a team of qualified professionals, but the workplace dissatisfaction will continue to limit the effectiveness of operations.
Additionally, there are concerns about the effectiveness and speed of CS&C’s operations. For example, in the past, US-CERT has been widely criticized for only sharing information provided by the private sector after considerable delays, though this criticism has decreased recently.[135] The GAO found in 2014 that, though federal entities are generally satisfied with US-CERT’s responses to incidents, it is hard to determine just how effective US-CERT is due to a lack of evaluation measures.[136] Additionally, while Einstein is continuing to spread across federal systems, unnecessary delays and bureaucratic barriers still exist. This was made evident during the 2014 Heartbleed vulnerability incident. While Einstein was able to detect the Heartbleed computer bug, Phyllis Schneck, the Deputy Under Secretary for Cybersecurity and Communications for the NPPD, stated that it took almost a week until some other government agencies let the NCCIC and Einstein search for problems.[137] Other concerns include the slow adoption of the ECS program, though the IG found that DHS is making headway on improving the program and is meeting the IG’s recommendations.[138]
The GAO has issued multiple reports noting significant flaws in cybersecurity measures and in incident response and mitigation procedures.[139] Similar to the example of Einstein and Heartbleed, DHS needs to have greater authority and more robust relationships with government organizations so that DHS can help those agencies secure their systems and respond to security incidents. The recent discovery of a major breach of the Office of Personnel Management (OPM) database, however, has raised questions about the efficacy of the Einstein program. It appears that OPM did not have access to the latest generation of Einstein, but experts still wonder why the existing program was unable to detect so much information being exfiltrated from government servers.[140] While Einstein is still an important tool in the cybersecurity arsenal, this major data breach should reinforce the idea that there is no silver bullet to cybersecurity.
CS&C also manages communications networks and emergency communication systems. The National Coordination Center for Communications maintains communications systems during natural disasters and after terror or cyber attacks.[141] The Office of Emergency Communications (OEC) on the other hand, works primarily with emergency responders throughout all levels of government to ensure that interoperable communications are available in the event of an emergency.[142] However, the IG reported in 2012 that only one of 479 DHS radio users could find and use a common channel to communicate with each other. When the radios were analyzed, 54 percent did not have the DHS Common Channel programmed into the radio, and 26 percent had other problematic settings. Similarly, 29 percent did not have the Federal Interoperability Channel programmed, and 45 percent had other flawed program settings for communicating over that channel.[143]
While some improvements have been made, the IG reviewed DHS’s progress and in May 2015 found that the IG’s recommendations were only partly implemented and that most DHS radio users could still not access the DHS common radio channel.[144] The IG recommended to the Under Secretary of Management that more authority be given to the OEC and other coordinating bodies to “ensure that components achieve interoperability,” though DHS disagreed with this recommendation. This recommendation is similar to Heritage’s recommendation for DHS management that centralized service offices receive more authority to ensure that all components are implementing department-level policy. With a stronger coordinating structure, the IG also recommended improving policies governing the standardization of DHS radio activities and settings.
Infrastructure Protection. The NPPD’s Office of Infrastructure Protection (IP) is the lead organization in the U.S. government for the protection of critical infrastructure.[145] The U.S. has 16 critical infrastructure sectors:[146]
- Chemical
- Commercial Facilities
- Communications
- Critical Manufacturing
- Dams
- Defense Industrial Base
- Emergency Services
- Energy
- Financial Services
- Food and Agriculture
- Government Facilities
- Health Care and Public Health
- Information Technology
- Nuclear Reactors, Materials, and Waste
- Transportation Systems
- Water and Wastewater Systems
DHS is responsible for 10 sectors; the IP is responsible for six (indicated in bold). The NPPD also coordinates critical infrastructure policies across all sectors, following the guidance of the National Infrastructure Protection Plan (NIPP) and PPD-21.[147]
To protect critical infrastructure, sector-specific agencies should:
- “Facilitate the public-private partnership across critical infrastructure sectors;
- “Develop strategic goals to mitigate risk and improve resilience;
- “Provide and promote education, training, information sharing, and outreach support;
- “Shape sector-specific goals that address physical, human, and cybersecurity risks and drive security and resilience activities and programs;
- “Provide, support, and facilitate technical assistance and consultations to identify vulnerabilities and mitigate incidents;
- “Implement the NIPP 2013 framework and guidance tailored to respective sectors;
- “Develop sector-specific plans with public and private sector partners.”[148]
While these sector-specific agency activities are primarily voluntary, agencies may also have additional regulatory authority to mandate certain activities. Within IP, the Infrastructure Security Compliance Division (ISCD) is one example of such authority, as it enforces the Chemical Facility Anti-Terrorism Standards (CFATS) governing the chemical sector.
CFATS is supposed to operate by ranking chemical facilities according to their level of risk, that is, the threats they face, the vulnerabilities in their security systems, and consequences of an attack on the facility. Once facilities are grouped into four risk tiers, each facility is required to improve its security by meeting 18 performance standards through a site-security plan or an alternative security program (ASP). While in theory this risk-based type of regulation is preferable to one-size-fits-all mandates, CFATS has fallen far short.
In April 2013, the GAO reported significant problems with the risk-based system that underpins CFATS. Specifically, the GAO found that in considering and analyzing risks, DHS did not consider economic consequences, failed to identify or include vulnerabilities, and assessed threats inconsistently. In other words, the risk assessment that is central to CFATS failed on all three elements of risk: threat, vulnerability, and consequences.[149] The GAO report also found that DHS outreach to chemical facilities was generally not useful.[150] The same report calculated that even if the ISCD dramatically increased its reviews of security plans, it would take between six-and-a-half years and nearly nine years to completely approve the plans, not to mention conducting compliance inspections and making changes in risk tiers.[151] In addition to these problems, the ASP program, which industry thought would be more widely used, has been restricted, forcing more low-risk facilities to undertake additional security precautions regardless of whether existing security upgrades could have been effective alternatives.[152] Finally, of the 18 CFATS standards, the ISCD struggled to create and implement the Personnel Surety Program, confusing chemical facilities and delaying the approval of security plans.[153]
In 2014, Congress tried to resolve some of these issues. The Protecting and Securing Chemical Facilities from Terrorist Attacks Act of 2014 attempts to clarify and expand the use of ASPs, and simplifies the personnel-surety standard[154] by allowing a chemical facility to use other government screening programs as a way to meet CFATS requirements.[155] In addition, the act attempts to speed up the approval process with expedited approval for lower-risk tiers. DHS has also taken action to shorten the backlog, though GAO has yet to report on the effectiveness of these changes.[156] While the act calls for a proper risk assessment, it is unclear whether DHS will be successful this time around.
Federal Protective Service. The NPPD is also responsible for protecting over 9,500 federal facilities across the U.S. With around 1,000 full-time law enforcement positions and 13,000 contractors, the Federal Protective Service (FPS) is a significant part of the federal security force, but it can also delegate security responsibilities and allow agencies and facilities to manage security themselves. The FPS is currently funded by fees it collects from the agencies and facilities it protects.[157]
Beyond the cybersecurity risks identified by the GAO (mentioned above), the FPS has significant challenges. According to Roll Call, between 2010 and 2012, the “GAO made 26 recommendations relating to FPS risk assessment programs and oversight of guards’ training, certifications and qualifications.”[158] As of April 2016, the GAO has at least 23 open recommendations for the FPS, with eight ranging back to 2012.[159] As mentioned, these areas in need of improvement center on how well the FPS assesses risk, budgets and plans, and manages and oversees its security forces and activities central to its protective mission. For example, the GAO found in September 2013 that five of 16 guard companies had not received active shooter training, while other companies’ guards had not been trained in the use of screening equipment.[160] The GAO reviewed a sample of guard files, also in 2013, and found that 23 percent were missing some “required training or certification documentation.”[161] Multiple recommendations concerning these issues remain unresolved. More recently, in a March 2015 report, the GAO found that the FPS was not managing its delegations of security responsibility effectively. The GAO reported that the FPS claimed that 62 delegations of security responsibility were active, but included 12 delegations that had expired or been rescinded.[162]
In what could be viewed as a significant vote of “no confidence,” a May 2014 DHS memo announced that the FPS would no longer be directly responsible for security at DHS headquarters.[163] While this was disputed by the FPS, such news is merely one of many concerns that the FPS must navigate if it is to improve its operations.
Biometric Identity Management. The NPPD’s Office of Biometric Identity Management (OBIM), called US-VISIT until 2013, is responsible for managing the U.S.’s biometric data system, the Automated Biometric Information System (IDENT). IDENT is used to collect biometric data from individuals as they enter the U.S. for a variety of immigration purposes as well as for counterterrorism and security purposes.[164] To these ends, IDENT is closely integrated with the FBI’s Integrated Automated Fingerprint Identification System (IAFIS).[165] IDENT, however, was created in 1994, and though it has made remarkable improvements over the years, DHS’s Chief Information Officer has seen continuation of this aging system as a growing risk due to increasing demands and technical limitations.[166] With that in mind, the NPPD is looking to begin replacing IDENT, which should lower maintenance costs and improve capabilities.[167] President Obama recommended that OBIM be shifted to CBP in his final budget request, as NPPD is not the best fit for the office.
Before moving this office, DHS should consider a larger-scale streamlining and upgrading of its vetting and immigration casework systems. With systems from CBP’s TECS, USCIS’s ELIS and asylum claims systems, NPPD’s IDENT, and other systems facing challenges or the need for updates, DHS should develop a more cohesive and integrated set of systems. One way this could be done is to embrace a person-centric model that allows DHS organizations, when investigating or vetting an individual, to query the person rather than various systems. A person-centric system would pull information from each DHS component so the investigator or adjudicator has all the necessary information in one place. The TSA is working on adopting this approach in its intelligence and screening efforts,[168] and other parts of DHS have considered such a system as well.[169] DHS would be wise to expand such efforts over the entirety of DHS and determine the resources that will be needed to implement such a system.
Actions for Congress. To improve the U.S.’s cybersecurity and security of critical infrastructure, Congress should:
- Implement cyber-threat and cyber-vulnerability information sharing. CISA allows the private sector and public sector to more easily share information with each other, benefitting both sides. By providing strong liability protection for shared information, businesses will be encouraged to share with the government as well as with other businesses.
- Help DHS improve and expand its ability to monitor government networks. The DHS-run Einstein intrusion-detection-and-prevention system has grown dramatically over the past decade. With better information sharing, Einstein’s ability to detect and prevent intrusions would be enhanced, but the system must connect to other sources, such as NIST’s NVD and DHS’s CDM. Additionally, Congress should encourage DHS to expand the traffic that Einstein monitors and the types of methodologies it uses to detect malicious activity. Congress should prioritize the continued improvement and expansion of the Einstein system. DHS needs the clear authority, relationships, and ability to work with other agencies in using Einstein and other cyber tools.
- Improve morale of DHS staffers. Morale at the NPPD is incredibly low, which makes it difficult to recruit and keep good employees, especially when private-sector cybersecurity jobs are available. Notably, pay is not the central issue in this survey. The lack of leadership, training, and performance-based rewards are blamed, and to the extent that Congress can do so through the budget process, it should mitigate these problems. For example, Congress should ensure that funding for performance-based rewards and training is sufficient. If DHS is to be an effective actor in defending U.S. cyberspace and critical infrastructure, more must be done to improve morale and maintain a highly skilled workforce.
- Reform risk assessments to capture all relevant information, including consequences, threats, and vulnerabilities. DHS has a history of conducting risk assessments poorly, and this systemic problem must be resolved. Not correcting this problem will mean that important security decisions are made with inaccurate and incomplete information. Trouble with risk assessments at the FPS and ISCD severely hamper the efforts of the NPPD to protect critical infrastructure.
- Improve interoperable communications policies. The OEC and coordinating bodies must have more authority to insert policy into each DHS component. Policies must also be improved to ensure that DHS radio users are able to communicate seamlessly with other DHS and federal officials, not to mention state and local officials.
- Return CFATS to a truly risk-based approach. A risk-based approach would allow chemical facilities and DHS to focus on the most serious risks. Instead of inflexible regulations that impose large costs on chemical facilities, a risk-based approach would also better respect market principles and allow businesses to manage risks in the most cost-effective manner. This means ensuring that DHS expands the use of ASPs, expedites security plan approvals, and improves risk assessments.
- Explore alternative funding structures for the FPS. The GAO recommended comparing alternative funding structures to ascertain the pros and cons of different approaches that include some level of direct appropriation.[170] Inserting a more stable source of income might improve the FPS’s budgeting and planning processes as well as improving the way it provides training to its officers. This should be explored by the FPS and the Congressional Research Service.
- Investigate integration of vetting and case management systems. Before moving OBIM to another subcomponent, DHS should consider how it could better integrate and update the entire DHS constellation of vetting and caseload systems so that users across DHS are better able to access all the relevant information on an individual.
To fund these activities, the Heritage budget recommends $3.3 billion for the NPPD.
9. Federal Emergency Management Agency
FEMA had a total budget after rescissions of around $15.5 billion in FY 2015 and FY 2016, and a request for just over $16.5 billion for FY 2017.[171] As the agency with the largest budget in DHS, FEMA is responsible for three major areas: (1) disaster relief and preparedness under the Stafford Act; (2) homeland security and emergency preparedness grants; and (3) the National Flood Insurance Program (NFIP). Each of these areas is in desperate need of reform, costing U.S. taxpayers large sums of money and not efficiently serving those who need FEMA. These programs have become political pork that communities and all Members of Congress have come to count on, making changes to these programs difficult. However, it is for just this reason that FEMA needs major reforms, so that these programs can get back to helping people and cease being political footballs and mechanisms for handouts.
Disaster Relief Fund. Throughout most of U.S. history, state and local governments were responsible for responding to nearly all disasters, regardless of the cause. Under President Ronald Reagan, FEMA averaged 28 federal disaster declarations a year.[172] After the passage of the Stafford Act in 1988, this number dramatically changed, with federal disaster declarations steadily rising, so that under President George W. Bush and President Obama, the U.S. has averaged around 130 federal disaster declarations a year.[173] The result has been that FEMA now responds to a disaster every 2.8 days and has needed ever more money to cover the costs of responding to growing numbers of disasters. The Stafford Act has at least two provisions that are to blame. First, the act shifts at least 75 percent of disaster response costs to the federal government.[174] In the event of a disaster, states normally have to pay for the costs of responding, but if the President declares the disaster worthy of federal assistance, at least 75 percent of response costs are covered by the federal government. The result has been that states now request federal help whenever they can, since it will bring federal dollars. This has created a vicious cycle as states respond to increased federalization of disasters by preparing less and setting less funding aside. As a result, states are less prepared for disasters, they request more government help, and the cycle is perpetuated.
The second problematic provision of the Stafford Act makes it far too easy for states to request disaster assistance. The act vaguely requires that a disaster be “of such severity and magnitude that effective response is beyond the capabilities of the State and the affected local governments and that Federal assistance is necessary,”[175] and that storm-related damages top approximately $1.40 per capita, which for several states is less than $1 million.[176] So even local disasters that are centered in one state and cost as little as $1 million can be considered federal disasters. This combination of easy-to-acquire federal assistance and the substantial monetary benefit of federal involvement puts FEMA in high demand, leaving it unprepared—both in terms of readiness and money—for truly catastrophic disasters where it is most needed.
Analysis of disaster declarations in 2013 and 2014 indicates that major savings can be had by reforming the Stafford Act. If the Stafford Act’s eligibility threshold had been increased to require $3 per capita in damages with a $5 million minimum threshold (under which a federal disaster is never declared) and a $50 million maximum threshold (over which a disaster declaration is always issued), approximately half of all major disaster declarations would not have been issued. According to the cost estimates made to justify a disaster declaration, not issuing disaster declarations for these disasters would save FEMA around $260 million in 2014 and almost $400 million in 2013.[177] Of the remaining disasters, the FEMA cost share should be reduced from between 75 percent and 100 percent to 25 percent with a greater cost share for large catastrophes. This system of funding will require states to take responsibility for more localized disasters. It will also ensure that FEMA is able to respond to disasters more effectively, and that it can save funds for catastrophic disasters. For disasters that top $5 billion, the cost-share provision should gradually increase as the cost of the disaster increases. This gradual increase in cost sharing should be capped at 75 percent once a disaster tops $20 billion. These thresholds should be properly indexed for inflation to rise over time and ensure that FEMA is most engaged in catastrophic disasters while returning responsibility for smaller disasters to the states.
A potential alternative to the thresholds listed above, which FEMA is currently considering, is the implementation of state and local disaster deductibles. By returning more of the initial costs to the states, states will have an incentive to be better prepared for disasters, and FEMA could reserve more of its focus and funds for larger disasters. This deductible system could even make use of private insurers, who are best positioned to understand the risks in a given state, what the state has done to mitigate those risks, and set the price of a state’s insurance premiums and deductible level based on such risk factors. While FEMA may have the authority to do this via regulation, Congress should also consider how such an effort might improve disaster preparedness and response.
Homeland Security Grants. FEMA is also responsible for administering various homeland security grant programs. These include the State Homeland Security Program (SHSP); the Urban Areas Security Initiative (UASI); Operation Stonegarden (OPSG); various transportation and port security grants; grants for hazard mitigation, such as Flood Mitigation Assistance; grants for firefighters and emergency personnel, such as the Staffing for Adequate Fire and Emergency Response (SAFER); and other preparedness grants, such as the Emergency Management Performance Grants (EMPG).[178]
While federal grants to state and local partners may be of value in some cases, the current structure does not adequately prioritize grants based on the risk they are trying to reduce. To the Obama Administration’s credit, it has recommended consolidating many of these grants into a new National Preparedness Grant Program that would allot grants in a more risk-based fashion.[179] Grant consolidation should be revisited by Congress and expanded to cover more grant programs. Grants that meet the greatest need in areas of high risk should be prioritized. These grant dollars should not be viewed as another entitlement to send back to each congressional district, but as limited homeland security funding that will alleviate the greatest risks.[180] Failure to prioritize grants weakens security and preparedness, and continues waste and abuse.[181]
In this process of moving DHS grants to a more risk-based allocation system, the grant programs must be evaluated to see which needs they are meeting and how well they are doing so. Grant programs that are found to be ineffective or unneeded should be cancelled. Heritage Foundation research has found that a variety of firefighter and emergency personnel grants, including SAFER as well as Fire Prevention and Safety (FP&S) grants and Assistance to Firefighter Grants (AFG), do not reduce fire casualties and merely subsidize local fire services.[182] With other more important and more effective areas where such funding could be spent, such grants are a luxury the U.S. cannot afford.
National Flood Insurance Program (NFIP). Originally created in 1968 to help reduce disaster relief payouts, the NFIP has ballooned today into a program that encourages development in high-risk flood zones. Today, almost all flood insurance is provided by the federal government, because it provides insurance at prices lower than the actuarially fair rate, that is, it subsidizes flood insurance, transferring tax dollars to those who build homes and businesses in flood zones. As a result, when the cost of flooding exceeds the revenue gathered by the program, FEMA ends up requiring a bailout with taxpayers on the hook, which as of 2015 totaled $23 billion.[183] By subsidizing building in these zones, the NFIP encourages more people to live in flood zones, increasing the potential losses to the NFIP and the taxpayer.
The Biggert–Waters Flood Insurance Reform Act of 2012 attempted to reduce this effect by making insurance rates more accurately represent the risk of the property and instituting a reserve fund. Congress limited this reform in 2014. Rather than taking additional steps to wind down government involvement in an industry where it does not belong, Congress backtracked and once again instructed FEMA to cap insurance rates and rate increases, thus not correctly accounting for risk, which would allow lower premiums.[184] By undoing and delaying some of the earlier reform, Congress has increased the cost of flood insurance to the average taxpayer. Senator Mike Lee (R–UT) proposed an amendment that would have required owners of second homes and vacation homes to pay higher rates, but Congress rejected his amendment, subsidizing coastal vacation homes at the expense of U.S. taxpayers.[185]
As a result, the GAO includes the NFIP in its High-Risk Series, finding that between 2002 and 2013, FEMA missed out on $11 billion to $17 billion in net premiums due to federal subsidies.[186] While the GAO points out multiple challenges that FEMA has in administering the NFIP, the GAO also notes that many of the challenges were created by Congress, such as requirements to complete multiple studies in short time frames, mandates that make it impossible for FEMA to run the program sustainably, and multiple changes to the law over the course of several years that stress FEMA’s administrative capability. FEMA is also challenged by the lack of flood-risk information with which to properly determine policies’ full-risk premiums.[187]
The NFIP is an inefficient, unnecessary, and costly government intervention into an industry that would otherwise function well. Insurers are capable of assessing risks based on geographic and weather-based phenomena. Homeowners in areas prone to forest fires, tornados, earthquakes, and other natural disasters can have that added risk built into their policy because insurers can use data on past events, together with home improvements or predicted changes in risk, to price insurance properly. In almost all cases, private flood insurers could conduct the same risk assessment and set prices more in line with the actuarial rate.
Critics of such an approach appeal to the hardship that homeowners in flood-prone zones will face as a result of higher, actuarially sound rates. But this argument is exactly why the NFIP should be terminated. By subsidizing living in higher-risk areas, the NFIP encourages more people to live there—increasing the destruction that individuals face, and increasing the costs to all taxpayers. Why should a farmer in Iowa, a rancher in Texas, or a salesperson in Denver pay for lower insurance rates for someone in Louisiana or Florida? Just as the government should not subsidize or be involved in insurance for tornado or snowstorm damages, FEMA should not be in the business of flood insurance. While there can and should be a transition period to allow private insurance to take the place of federal insurance and to lessen the shock to homeowners, this should be a relatively short period, no longer than four years. The NFIP should be maintained only for the rare cases where private insurance is not available, and it should be done at an actuarially fair price.
Actions for Congress. To stop the over-federalization of disasters, improve the focus of FEMA grants, and improve flood insurance provision in the U.S., Congress should:
- Reduce the federal share for all FEMA declarations to a 25-percent cost share. This way, at least three-fourths of the costs of a disaster are borne by the taxpayers living in the state or states where the disaster took place. For catastrophes with a nationwide or widespread regional impact—such as Hurricane Katrina—a relief provision would provide a higher federal cost share if the total costs of the disaster exceeded an inflation-adjusted threshold that began at $5 billion. Starting at $5 billion, the cost share would gradually increase as the cost of the disaster increases, maxing out at a 75 percent cost share when a disaster cost more than $20 billion.
- Modify the Stafford Act to establish clear requirements that limit the situations in which FEMA can issue declarations. This should include eliminating some types of disasters from FEMA’s portfolio entirely. Another way is to raise the minimum-dollar threshold for requesting disaster declarations. Increasing the threshold to a minimum of $5 million (and a maximum of $50 million); increasing the per capita threshold to $3 per capita; and properly indexing these sums for inflation would significantly reduce the number of events that would warrant a federal disaster declaration. FEMA is currently considering a disaster deductible system for states that could also achieve similar results.
- Consolidate homeland security and emergency preparedness grant programs and allocate funds in a risk-based manner. Rather than treating grants as federal dollars that should be spread around, federal grant dollars should be focused on the highest-risk areas and issues. As part of this consolidation, grant programs should be evaluated, and ineffective ones, such as SAFER, FP&S, and AFG, should be cancelled.
- Begin to transition nearly all users of the NFIP to private insurance. The NFIP should be wound down. After one year, the NFIP should begin to phase out insurance for lower-risk insured groups (NFIP designations B, C, and X), followed by phasing out NFIP insurance for increasingly high-risk properties (designations A, AE, V, and VE).[188] Within four years, the NFIP should exist only to serve a select few homeowners who are unable to acquire insurance, not because the cost is too high, but because it is not offered in their area. These properties, however, should not be subsidized; these property owners should pay a fee at a rate that is actuarially as fair as possible.
To fund these activities, the Heritage budget recommends $13.5 billion for FEMA. Specifically:
- $1.5 billion for federal assistance, including cutting ineffective grants like AFG, FP&S, and SAFER, and streamlining all grant programs into one, which will provide grants in a risk-based manner, not based on parochial or political interests.
- $5.3 billion for the Disaster Relief Fund, made possible by the reforms to the Stafford Act that increase eligibility requirements for FEMA funds and decrease the amount of FEMA funds made available, especially for smaller disasters.
10. U.S. Citizenship and Immigration Services
The USCIS had a budget of approximately $3.2 billion in FY 2014, while in FY 2015 its budget was set to jump to around $3.77 billion as a result of increased revenue from President Obama’s executive action on immigration. With the executive action enjoined, the funding for FY 2016 was only $3.61 billion, though the President requests just over $4 billion for FY 2017. The analysis in this Special Report assumes that President Obama’s executive action will be struck down by the Supreme Court. Due to the USCIS’s mostly fee-based funding system, the exact level of revenue, and therefore expenditure, is never entirely clear in advance.
The USCIS is tasked with processing and adjudicating the millions of immigration-related requests made every year. These include work and study visas, E-Verify, green cards or permanent residence, and integration and citizenship. Except for E-Verify, these tasks are paid for with application fees paid by immigrants or those looking to study or work here temporarily. As a result of President Obama’s Deferred Action for Childhood Arrivals (DACA) and Deferred Action for Parental Accountability (DAPA) programs, the USCIS is also charged with providing illegal immigrants with the so-called deferred action status, a pseudo-legal status undefined and not authorized anywhere in the Immigration and Nationality Act, but which has come to mean protection from deportation and receiving work-authorization documents and Social Security numbers.
The President’s most recent executive action to expand DACA and create DAPA has been the source of considerable controversy as both programs upend the clear meaning of U.S. immigration laws. Rather than enforcing existing laws against illegal presence in the U.S., DACA and DAPA actively work to protect illegal aliens from deportation. Further, despite clear prohibitions of illegal immigrants working in the U.S., these programs turn the prohibitions on their head by authorizing labor and providing Social Security numbers, with all the benefits those entail, including driver’s licenses and tax credits.[189] By not only tolerating, but actively rewarding illegal presence, DAPA and DACA are encouraging additional illegal entries, costing U.S. taxpayers more and more.
The result was a threatened slowdown of DHS operations in February 2015, with many Republicans seeking to prevent the USCIS from using any of its funding to carry out the President’s unlawful actions. Congress, however, did not stand its ground, and surrendered to the executive overreach. As a result, the rule of law has been permanently harmed, with the President able to defy congressional action (or inaction) and existing law in furtherance of his own policy preferences. This has created a dangerous precedent for future Presidents, who might use this exact logic to nullify laws with which they disagree, including tax, environmental, labor, privacy, or a host of other laws. Only Federal District Judge Andrew Hanen’s injunction, backed up by the higher courts, stands in the way of this constitutional usurpation of legislative authority.[190]
Moving forward, Congress must again stand for its constitutional responsibilities and authority—failure to do so portends greater harm than just this current immigration action. Congress’s only tool in this fight is the power of the purse, and failure to use it condemns it to growing irrelevance and fewer checks on executive power.
Effective and Fair Adjudication of Immigration Benefits. Beyond this current fight over the President’s executive action, the USCIS is in need of other reforms to make it work more efficiently and better adjudicate U.S. immigration laws. While there are large backlogs for various visas due to statutory prescriptions, the USCIS has struggled to adjudicate visas, modernize the visa application system, and prevent abuses of the system.
Kenneth Palinkas, president of the National Citizenship and Immigration Services Council that represents around 12,000 USCIS officials, cited multiple serious problems with the USCIS that should be fixed “before any amnesty proposal is brought forward.”[191] He described these problems as:
- “[A] lack of mission support [including] the failure of our software system.”
- “Failure to protect taxpayers from abuses of the welfare system by those granted immigration benefits.”
- “Administrative orders that require us to grant immigration benefits to those who, under law, are not properly eligible” and “approval quotas placed on adjudicators that emphasizes clearing applications more than vetting them.”
- “A management culture that sees illegal aliens and foreign nationals, not US citizens and taxpayers, as the customer. We believe in treating all with respect and always will, but our agency’s focus must be keeping the country safe and secure on behalf of the American people.”[192]
Over the past several years, there have been multiple high-profile examples of improprieties in the way the USCIS adjudicates cases. Before DACA began, a January 2013 report by the IG revealed that USCIS officials were pressuring employees to approve various immigration applications that should have been denied. Furthermore, employees complained of not having enough time to complete interviews of applicants, “leav[ing] ample opportunity for critical information to be overlooked.”[193]
When the USCIS began to process DACA applications, pressure on USCIS employees grew. As with more permanent forms of amnesty, DACA recipients were required to undergo supposedly stringent background checks. E-mails obtained through Freedom of Information Act requests, however, show that several months after the start of DACA, the USCIS moved to a “lean and lite” system of background checks that were not as detailed as the DACA policy itself required. Additionally, the e-mails revealed “managerial pressure not to turn any alien applicant away for lack of ID, including [an] explicit directive in an Oct 3 memo” to this effect.[194]
More recently, a multiyear investigation by the DHS IG found that the current Deputy Secretary of DHS and former head of the USCIS, Alejandro Mayorkas, gave special treatment to high-ranking political officials in securing EB-5 visas for investors and job creators. According to the IG, Mayorkas “exerted improper influence in the normal processing and adjudication of EB-5 immigration program benefits.”[195] The most notable beneficiaries of Mayorkas’s improprieties included then-Senate Majority Leader Harry Reid (D–NV), and former Pennsylvania Governor Ed Rendell (D). Anthony Rodham, brother of then–Secretary of State Hillary Clinton, and Terry McAuliffe (D), a former Clinton fundraiser who is now governor of Virginia, also received special access to EB-5 visas.[196]
Despite the ongoing investigation, Mayorkas was promoted by President Obama in 2013. Although the IG found no broken laws, this behavior is not what the U.S. should expect from its senior government officials. Homeland Security Secretary Jeh Johnson doubled down in support of Mayorkas,[197] and Mayorkas himself stated that a “complete and total repudiation of the allegations against [him] is the only correct and just conclusion.”[198]
Manipulation of security and screening procedures and pressure on employees to approve applications is obviously wrong. If such behavior occurred in the private sector, it would likely be grounds for legal or regulatory action by the government. Indeed, U.S. Investigations Services, a federal contractor that handles background checks for those seeking employment with the federal government, currently faces legal action from the Department of Justice for taking shortcuts with its background checks on behalf of government customers.[199]
Workplace Enforcement of Immigration Laws. The USCIS also handles the E-Verify program that verifies the work authorization of an individual. E-Verify can quickly determine with great accuracy the authenticity of the personal information and credentials offered by new hires. In general, the employer will use a computer to submit certain basic information concerning the employee (name, date of birth, Social Security number) to the government. The information is securely transmitted to DHS and the Social Security Administration, and DHS checks the information to determine whether it corresponds to a U.S. citizen or to a work-eligible immigrant. In most cases, DHS can check and confirm the employee information and transmit a definitive reply to the employer within seconds.
Under federal law, the use of E-Verify is optional for businesses, except for federal government contractors. However, some states, such as Arizona, have made the use of E-Verify mandatory and imposed a series of penalties on employers who knowingly employ “unauthorized aliens.” This includes suspension of the employers’ business licenses, an incentive for complying with the law. The Arizona requirement was upheld by the U.S. Supreme Court in 2011.[200] States, despite arguments to the contrary, play a key role in the enforcement of federal immigration law.[201]
In FY 2013, E-Verify automatically confirmed 98.81 percent of workers, with another 0.22 percent confirmed after disputing an initial mismatch, which usually took little more than a week to resolve.[202] That leaves just under 1 percent of cases with a non-confirmation.[203] E-Verify’s accuracy has increasingly improved, with one of the most recent studies, from 2012, finding that only 6 percent of final non-confirmations were erroneous.[204] Since about 1 percent of cases result in final non-confirmations, this means that approximately 0.06 percent of all E-Verify cases end in erroneous non-confirmations. The system also provides a simple and rapid mechanism for individuals to self-check their own status and discover any errors in their work authorization in order to prevent erroneous non-confirmations.[205] On the other hand, estimates from 2009 found that around 3.4 percent of confirmations were erroneous, mostly due to identity fraud.[206] Continuing to improve E-Verify by cutting down on errors and tentative non-confirmation-resolution times is important for encouraging business adoption of E-Verify. Additionally, working to combat identity fraud within the program will also improve E-Verify.
Refugees and Security. The USCIS is responsible for adjudicating refugee and asylum claims and admissibility to the U.S. as part of the larger U.S. Refugee Admission Program (USRAP), primarily administered by the State Department. While the U.S. can and should continue to help those in need, security must remain a paramount concern. Following the influx of Syrian refugees and migrants into Europe in 2015, the Obama Administration increased the number of refugees the U.S. would accept from 70,000 in FY 2015 to 85,000 in FY 2016, and a planned 100,000 for FY 2017. The Obama Administration has pledged to reserve at least 10,000 spots for Syrian refugees, a move that drew security concerns, concerns that were heightened following the terrorist attack in Paris, which involved at least one terrorist who entered Europe through the migrant pathway.[207] Subsequently, two immigrants who entered the U.S. as refugees have been charged in separate terrorist incidents. Omar Al Harden, who came to the U.S. from Iraq in 2009, is thought to have been planning to bomb two Houston malls,[208] while Aws Mohammed Al-Jayab entered the U.S. as a refugee in 2012, and immediately began looking to return to Syria to fight for Islamist terror organizations. He was successful in getting to Syria in 2013 and returned to the U.S. in 2014.[209]
Such events have raised real concerns about the U.S. refugee system and its ability to vet refugees. The vetting process includes checking databases across the U.S. government, including those in the Departments of State, Homeland Security, and Defense, the Drug Enforcement Administration, the FBI, the National Counterterrorism Center, as well as Interpol. There is also a USCIS refugee interview conducted by special officers who receive some additional training on country-specific issues. For example, Syrian refugee officers must undergo a one-week training course on Syria-specific issues, including classified information.
In addition, the refugee process requires a Security Advisory Opinion to be completed by the FBI and the intelligence community on many refugee applicants who are considered higher risk. Similarly, interagency checks (IACs) are constantly being done in connection with a wide range of U.S. agencies. In areas of greater concern, as is currently the case with Syria and Iraq, additional scrutiny can be applied to applicants through an enhanced review process that puts additional security and intelligence resources at the disposal of adjudicators.
While the vetting process used by USRAP is the most thorough of any method of entering the U.S., it also faces greater challenges than other methods. As multiple U.S. officials have noted, vetting against intelligence databases can only provide as much information as in the database; that is, if there is little information about an individual in the databases, such screening will not be able to tell refugee officers much.[210] Since many nations that produce refugees are chaotic, war torn, or have an unfriendly government, the U.S. has limited ways of gathering information with which to vet an individual. The limitations in intelligence vetting puts more pressure on refugee interviewers to corroborate information and detect suspicious behavior.
Given such risks, it is incumbent on the Administration to regularly inform Congress about the risks within the refugee vetting process and how it is mitigating those risks. While the refugee issue is a passionate one, USCIS and Congress should be guided by clear risk assessments that inform continuously refined methods for handling risk.
Challenges to the Visa System: IT and Fraud. Other failures, most notably of USCIS’s IT system and protecting Americans from dangerous individuals and immigration abuses, are areas ripe for commonsense, good-governance reform. Improving the effectiveness of USCIS should be a priority for any President who wants to better administer the U.S. legal immigration system in order to support the U.S. economy, protect the security of Americans, and make it easier for foreign workers to come here legally.
To work, study, or permanently reside in the U.S., foreign individuals must acquire the appropriate visa. For individuals living around the world, the slowness of the U.S. paper-based system is a hindrance to coming to America. An online system would support the public diplomacy and economy of the U.S. by making it easier for foreigners to come to and remain in the U.S.
The U.S. government, however, has struggled to create an online system to handle most immigration functions. Called a “transformation” of the application system, the Electronic Immigration System (ELIS)—on which the USCIS has $1.2 billion in sunk costs, well above the original $500 million originally allocated for the five-year period—missed most major milestones.[211] As of March 2016, users of ELIS could apply for only two of around 90 immigration benefits online, and could pay the $165 USCIS Immigrant Fee, but not dozens of other potential fees.[212] DHS is working on rebuilding the system and in early 2014 issued the first of multiple contracts to new vendors.[213] As a result, the program will continue to face challenges in the existing system while trying to transition to the new system. Even with this transition, the Inspector General found hundreds of millions of wasted dollars and many continuing problems. While $1.2 billion have been spent so far on the program, the total lifecycle cost is now estimated at $3.1 billion. Furthermore, the IG notes that he is “perplexed” and “disappointed” by USCIS’s resistance to his investigation and recommendations for improving the program.[214] It is considered a “medium-risk investment” by DHS’s Chief Information Officer.[215]
A simple but important reform that this and future Administrations should undertake is better managing the transformation of USCIS’s application system. Other policies, including amnesty, expanded numbers of worker visas, and changes to the number and allocation of green cards, will all increase the number of individuals applying to USCIS, thus adding to USCIS’s workload. Without the capability to handle this increased applicant base, security and procedural standards, wait times, and USCIS budgets will all suffer. Such a reform is important as well as eminently doable if proper attention and oversight are given to the issue. More specifically, DHS should ensure that acquisition best practices, as laid out in a 2011 GAO report on ELIS, are closely followed in order to develop reliable plans for schedules and costs.[216]
While USCIS should make it easier for immigrants to come to the U.S. through an effective Web-based application process, USCIS must also prevent immigration fraud, which opens the U.S. to dangerous individuals and groups as well as additional costs.
A recent example of fraud was uncovered by the House Judiciary Committee, which discovered an unreleased government report that found that as many as 70 percent of asylum cases in 2005 had an indicator of fraud.[217] While changes in the immigration system have occurred since then, Louis Crocetti, a former head of the Fraud Detection and National Security office at USCIS, said he was “unaware of any immigration benefit fraud assessments, risk assessments, studies, or any other fraud-based research and analysis being performed since the last BFCA [Benefit Fraud and Compliance Assessment] was conducted in 2008,” not just on asylum fraud but on fraud related to all forms of entry.[218]
The GAO studied this issue in 2015 and agreed that “[w]ithout regular assessments of fraud risks, USCIS and EOIR lack reasonable assurance that they have implemented controls to mitigate those risks.”[219] The GAO also found that much of their case load was handled via paper files, which made fraud investigations logistically difficult. Additionally, even the officers responsible for fraud investigations in the Fraud Detection and National Security Directorate felt they had limited guidance on the issue of fraud. On top of, and perhaps because of, such limited fraud detection, asylum claims have more than doubled between FY 2010 and FY 2014.[220]
Those who are granted asylum immediately receive work authorization; the opportunity to acquire derivative asylum visas for a spouse and minor children; and job and English language training, followed by access to a green card after one year and the opportunity to apply for citizenship four years later.[221] Asylees are also exempt from “public charge requirements”; that is, they do not have to be economically self-sufficient in order to obtain a green card, and have access to several forms of welfare, including Temporary Assistance for Needy Families, food stamps, and Medicaid.[222] Such benefits for asylees comport with Americans’ values of human rights and protecting those who cannot return to their home country for fear of persecution and repression. This generosity is not just a moral or principled position, it also furthers American public diplomacy by reinforcing the image of the U.S. as a beacon of freedom.
As can be the case with generosity, however, some take advantage of it. The many benefits the U.S. provides asylees are more than most individuals could ever dream of in their home countries. While the U.S. taxpayers have no problem helping those in need, they do take issue with paying for those who came here fraudulently and then receive redistributed tax dollars.
Despite the costs of fraud, USCIS officials face significant “pressure…to rubber stamp applications.”[223] Combined with few in-depth fraud investigations occurring within USCIS for any types of visas or requests to enter the U.S., taxpayers are left on the hook for the costs of such fraud, and the security of the U.S. is degraded. In addition to ceasing pressure on USCIS officers to rubber-stamp cases, DHS should reboot credible and public fraud-investigation and fraud-prevention measures.
Patriotic Assimilation Versus Multicultural Partition. USCIS is also responsible for promoting the assimilation of immigrants into U.S. culture and providing citizenship. Under President Obama, this priority has waned into a glorified mechanism to preach political activism that tries to divide immigrants from the rest of U.S. society. As part of his executive action on immigration, President Obama called for a Task Force on New Americans, which created a deeply flawed strategic plan[224] for integrating immigrants. Heritage’s Mike Gonzalez analyzed this plan and found that:
The strategic plan is replete with calls for (1) the “receiving communities” to change so that they can celebrate and accommodate the immigrants’ “diverse linguistic and cultural assets,” rather than the traditional view (and three-century reality) of immigrants becoming Americans over time by assimilating into the nation’s unique culture and developing patriotic sentiments; (2) federal and state government agencies to sanction “diverse cultural practices” rather than maintaining standards and norms that are equally applicable to all citizens; (3) making citizenship easier to attain, rather than the process being a more meaningful, transformative experience; and (4) “bi-literacy and dual-language learning” in order to “maintain native language proficiency to preserve culture” rather than schools performing their traditional job of promoting a shared cultural experience for all Americans. The plan also (1) accuses schools and agencies that supposedly prevent non-English speakers from having “meaningful access to federally funded programs” of violating the Civil Rights Act’s prohibition of discrimination against protected classes; (2) draws no distinction between citizen and non-citizen, lawful or unlawful resident; and (3) calls for distributing millions of dollars to liberal groups favorable to President Obama.[225]
The task force’s recommendations, in other words, make it easier to turn the United States into “more and more a hodgepodge of folks” in the President’s own words—one, moreover, where group differences become entrenched and permanent.[226]
This runs against the very essence of America’s history, with leaders as varied as George Washington, Thomas Jefferson, James Madison, Theodore Roosevelt, Woodrow Wilson, Ronald Reagan, and many others proclaiming the importance of assimilation and helping immigrants become Americans.[227]
Actions for Congress. To improve USCIS and the adjudication of immigration benefits, Congress should:
- Reject political influence in the visa-adjudication process. When the President’s executive actions force USCIS employees to cut corners, and high-ranking politicos are able to wield their influence to obtain green cards for their friends and preferred businesses, the U.S. effectively has a two-tier immigration system—one that serves the well-connected and special-interest groups, and one that deals with everyone else. Basic good governance requires that this sort of corruption and corner cutting not exist. Congress should require the IG to conduct an ongoing investigation into how political preferences and influence are pressuring USCIS employees to bend the rules.
- Ensure proper vetting in the refugee system and beyond. To ensure that those entering the U.S. as refugees do not pose a threat to the homeland, Congress should demand that the Administration provide Congress with regular risk assessments on the refugee program developed by the intelligence community. Based on these assessments, the Administration should also provide a plan for managing these risks. Given the potential limitations of intelligence databases, greater training for refugee officials should be considered.
- Restart comprehensive immigration-fraud evaluations. The U.S. is a generous nation that provides many people with immigration benefits, but there are too many who abuse the system. Given the value of U.S. visas and citizenship, the U.S. should do much more to investigate fraud, both on a case-by-case basis as well as through more comprehensive risk assessments and investigations.
- Strengthen E-Verify against identity theft. E-Verify prevents unauthorized workers from being employed, but one flaw with the system is that those using legitimate Social Security numbers acquired through identity theft can be authorized. The Social Security Administration should be required to work with the E-Verify system to identify cases where Social Security numbers are being used in multiple places or in suspicious ways.
- Reform the USCIS’s funding mechanism. To help USCIS engage more in fraud prevention, acquire better IT systems such as ELIS, and improve other administrative functions, the USCIS funding model should be changed. Currently, only E-Verify is funded by appropriations. Congress should move administrative parts of the agency to more regular appropriations to ensure that the funding of basic functions are dependent on the level of visa revenues.
- Promote real assimilation. Becoming an American should be a deeply meaningful experience that instills immigrants with love of America and her values. Current integration measures portray citizenship as little more than a legal right to a U.S. passport. This must change. USCIS must retool its integration efforts and not focus on multiculturalism, diversity, and activism as the desired values, but on patriotism, American principles, and civic education.
To fund these activities, the Heritage budget recommends $3.7 billion for USCIS.
11. Federal Law Enforcement Training Centers
The Federal Law Enforcement Training Centers’ (FLETC) FY 2016 budget of $244 million fell slightly from the FY 2014 and FY 2015 levels of $258 million, with President Obama requesting $242 million for FY 2017. The FLETC are a unique part of DHS that is entirely dedicated to training federal, state, local, and even international law enforcement, in a variety of skills and situations. Given the large size of the U.S. and that, as of 2008, it had around 810,000 state and local law enforcement officers (with more than 400,000 support staff),[228] the FLETC play an important role in preparing these officers and staff for the future.
With primary facilities in Georgia, South Carolina, New Mexico, and outside Washington, DC, as well as other partner and support facilities in Los Angeles, Washington, DC, and Orlando, the FLETC provide training in areas as varied as:
- Marksmanship,
- Active shooter threats,
- Forensics,
- Medical care,
- Vessel and boat boarding,
- Computer network investigation,
- Legal and use of force,
- Drug law enforcement,
- Critical infrastructure security,
- Non-lethal weapons, and
- Vehicle and driving training.[229]
In addition to training law enforcement officers in these areas, FLETC also offer several “train the trainer” programs that improve other training efforts across the U.S. To better serve the law enforcement community, the FLETC’s Online Campus provides law enforcement training resources via the Internet. For FY 2015, the FLETC reported that it “trained 65,341 law enforcement personnel, including 7,344 state and local law enforcement officers and 1,286 international law enforcement personnel.”[230]
Despite the importance of training at the FLETC and other DHS subcomponents, the IG found that DHS has consistently failed to report training costs. The IG found that of the approximately $1.4 billion allocated for training in the FY 2014 budget, DHS had only reported $1.9 million to OPM as required and the DHS CFO could only account for $267.6 million.[231] This is not the first time DHS has been criticized for such management practices, as concerns have existed since 2003, including the 2015 GAO High Risk report. While the FY 2016 appropriation includes funding for a modernized finance system and other reporting policy changes, Congress must demand that DHS be able to complete basic reporting requirements.
Actions for Congress. Since state and local law enforcement officers are often the first to respond to and deal with a crisis, such as an active shooter, DHS should expand “train the trainer” programs and direct the training of state and local officers. To continue and further the FLETC mission, the Heritage budget recommends $300 million, which should be spent on expanding operations. Additionally, DHS has had multiple studies and working groups that studied training expenditures and efficiencies, but has failed to act on such studies’ recommendations.[232] DHS should be required to further integrate training centers, looking for training facilities operated by other agencies that could be consolidated and operated by the FLETC.[233]
12. Science and Technology Directorate, Domestic Nuclear Detection Office, and Office of Health Affairs
The Science and Technology Directorate (S&T) received just over $1.2 billion in FY 2014 and $1.1 billion in FY 2015, falling to $787 million FY 2016, with President Obama’s budget request for FY 2017 seeking around $760 million. This significant decrease is due to the completion of funding for the new Bio-Agro Defense Facility in Kansas. S&T is the primary research-and-development arm of DHS, but as the Congressional Research Service concluded, “despite several restructurings and close congressional oversight, the S&T Directorate continues to face difficulties in meeting congressional expectations.”[234]
S&T Organization. S&T is broken up into multiple groups, each with a different focus:
- The First Responder’s Group conducts R&D to provide the emergency preparedness and response community with products specific to their missions;[235]
- The Research and Development Partnership Group works with federal, academic, and private laboratories on R&D activities and projects;[236]
- The Homeland Security Advanced Research Projects Agency (HSARPA) develops advanced technologies and capabilities to better equip and prepare homeland security officials in the field;[237] and
- Other offices, including the Capability Development Support Group, which defines mission needs, finds cost-effective solutions, and evaluates solution outcomes.[238]
The Congressional Research Service notes that these groups have no statutory basis and have been reshuffled regularly, usually with every new Under Secretary for S&T.[239]
Too Many Research Programs, Not Enough Focus. Despite these reorganizations, one significant problem with S&T research is that it does not adequately meet mission needs or benefit national security.[240] According to the GAO, DHS components that were surveyed “consistently said they were aware of few or no products that S&T had transitioned from one of S&T’s R&D projects to their respective components.”[241] As a result, S&T customers are likely to view S&T as not meeting end-user needs.[242] In the descriptions for the various parts of S&T, it is clear that the department is working to align research programs with mission needs, but S&T will need to consistently ensure that research programs are properly aligned with DHS-component needs.
The current Under Secretary, Dr. Reginald Brothers, has sought to address this issue by reducing the overall number of research programs in order to ensure that more attention is paid to the remaining programs. Under Brothers, S&T also started a pilot program that assigns S&T researchers to components’ laboratories in order to give researchers a better understanding of what is occurring at, and what is needed by, that component.[243] It is not yet clear that these changes will be sufficient to deal with the problem, but seeking to better understand and focus on the needs of DHS components, S&T’s primary customer, is a step in the right direction.
S&T and the Private Sector. A related issue with which S&T has struggled is coordinating research within DHS and with the private sector. As with many government research activities, there are often concerns that government research is duplicating work by other government organizations or the private sector. Responsible for research within DHS, only in September 2014 did S&T define what “research and development” means for the department,[244] bringing it in line with the Office of Management and Budget’s definitions.[245] Poor coordination of research activities not only harms the usefulness of end products in meeting mission needs, but also “makes it difficult to oversee activities across the department” and appropriately allocate resources.[246] In fact, the GAO found in 2012 that S&T did not know how much all DHS components were spending on R&D.[247] S&T has developed a definition of R&D and is working to encourage interagency communication and now must take additional steps to track R&D spending and ensure that spending is coordinated and not unnecessarily duplicative.[248]
S&T must do more to ensure that it does not duplicate the work of the private sector. The U.S. private sector is constantly striving to develop new products that are of interest to DHS personnel or state and local officials. From private cybersecurity and technology innovations to disaster response equipment, the U.S. private sector is the most powerful force for innovation in the world. S&T, however, may not always know of technologies or products available in the private sector that could meet DHS’s general needs or specific requirements. As a result, S&T’s office of Research and Development Partnerships has begun focusing on what it calls “technology foraging,” which seeks out existing or emerging technologies that could be adapted to meet DHS’s needs. This effort should be expanded as it costs the government less and will likely be faster than brand-new research and development.
SAFETY Act. A way to further encourage private-sector innovation is to expand the Support Anti-Terrorism by Fostering Effective Technologies Act. Passed as part of the Homeland Security Act of 2002, the SAFETY Act provides liability protection for sellers of qualified anti-terrorism technologies (QATTs) whose products or services may help prevent or mitigate a terrorist attack.[249] This protection is necessary so that the private sector does not fear being sued if its products are deployed and a terrorist attack occurs anyway.
The SAFETY Act provides different levels of certification to different products depending on their effectiveness. QATT certifications can be extended to products and services such as:
- Threat and vulnerability assessment services,
- Detection systems,
- Blast mitigation materials,
- Screening services,
- Sensors and sensor integration,
- Threatening object detectors,
- Decision support software,
- Security plans/services,
- Crisis management systems, and
- Venue security.[250]
The SAFETY ACT has resulted in certification of hundreds of technologies and services since its creation, increasing innovation and security. The U.S., however, is not the only country producing advanced and novel security services and technologies. By working with other countries, the U.S. can benefit from more products and also increase the market for U.S. products. To makes this happen, the U.S. should work with allies and partners on a bilateral basis to extend reciprocal liability protection regimes.[251 ]
A good potential pilot country for this expansion of the SAFETY Act would be Israel, which has a vibrant security industry, a relatively similar legal system, and a small economy. After working out the details and seeing how the pilot program works, the U.S. could then consider expanding the program to other allies, such as Canada and Great Britain.
Employee Morale. Another issue with which S&T has struggled is employee morale. S&T was tied with ICE as the worst office in the federal government for which to work, according to the Partnership for Public Service’s annual survey.[252] Morale and workplace satisfaction issues seem to be at least somewhat connected to S&T’s larger performance problems. Be it innovation, teamwork, strategic management, performance-based rewards, empowerment by leaders, or how well employees’ skills match their mission—employees all expressed significant dissatisfaction with how S&T handles these issues. S&T employees expressed negative feelings for other non-performance or mission-oriented issues, such as pay and support for diversity.
Domestic Nuclear Detection Office. Currently, the Domestic Nuclear Detection Office (DNDO), as its name implies, focuses on domestic nuclear forensics and detection capabilities. With a budget of approximately $347 million in FY 2016, the DNDO works with partners across the government as well as the private sector and academia to increase and improve the research, development, and use of nuclear-radiation-detection technologies. To this end, it has been successful in working with the CBP to ensure that 99.8 percent of incoming U.S. sea cargo containers are screened through a radiation portal before leaving the port. The DNDO also conducts various exercises with other agencies, such as law enforcement, to improve the use of detection equipment. The DNDO is pressing forward with a new Securing the Cities program intended “to enhance the capability of all our partners to detect and interdict dangerous radiological and nuclear weapons or materials in major metropolitan areas.”[253] The DNDO faced some challenges in the past but more recently has generally received bipartisan praise.[254] Despite its successes, the DNDO could improve its R&D by more explicitly tying its research investments to those gaps that it seeks to close.[255]
Office of Health Affairs. Another similar R&D-focused organization is the Office of Health Affairs (OHA), which focuses on biological and chemical incidents. With its budget of $125 million in FY 2016, the OHA’s main program, BioWatch, detects biological agents in high-risk areas, such as subways,[256] but its third generation was cancelled due to a price tag as high as $3 billion and technical challenges.[257] Despite these challenges, the need for early detection of a biological agent remains real and the OHA is left running the legacy BioWatch second generation. Other than a few planning and advisory roles, the OHA currently lacks a clear vision for what its future should entail.
To this end, DHS is considering reorganizing the way it manages R&D. Currently, other organizations, including the DNDO, the OHA, the Coast Guard, and the CBP, also conduct research that is supposed to be coordinated by S&T. Past reorganization efforts have considered moving the DNDO and the OHA into S&T to benefit from greater efficiencies of a single R&D organization. Another idea, proposed by DHS, is to merge the DNDO, the OHA, and possibly parts of other organizations into a Chemical, Biological, Radiological, Nuclear, and Explosive (CBRNE) Directorate. However, given the challenges that the S&T currently faces, a reorganization is not necessarily the solution. Better policy and formal coordination are less disruptive fixes to the problems facing S&T right now.
As for a CBRNE-focused organization, it may seem appealing on its face, but it overlooks a more serious need for the U.S. government to do a far better job coordinating CBRNE functions. The Environmental Protection Agency,[258] the Department of Health and Human Services,[259] the Department of Defense,[260] and other agencies share responsibilities with DHS for preparing and responding to different CBRNE incidents. Across the government, the U.S. needs to take the possibility of a CBRNE disaster more seriously, establishing resources, creating strategies and policies that cut across organizational lanes, and establishing a clearer coordinating authority and structure. While DHS has a significant role to play in such reforms, such reform is beyond the scope of this Special Report.
Actions for Congress. While the leaders of DHS’s R&D organizations have taken some positive steps toward improvement, their work is far from over.[261] Morale improvement, coordination of research with mission needs, and greater department-wide coordination of research must be priorities. To meet these objectives, Congress and the Administration should:
- Develop clear policies for overseeing R&D. With S&T just now defining R&D, S&T and other DHS components must properly report and account for spending on their research activities. This should feed into a mechanism for tracking R&D projects and total expenditures. While S&T has taken preliminary steps to assign roles and responsibilities for coordination of R&D projects, Congress should oversee these new guidelines to ensure that relevant agencies are fulfilling their responsibilities.
- Reject pork in R&D missions. R&D is a common area in which Congress mandates certain pork-barrel projects that benefit parochial interests in Members’ districts regardless of the wisdom of such an investment. While Congress can and should oversee spending efforts, it should not insert political and parochial interests to the detriment of actual R&D.
- Focus on primary customers—DHS components. While S&T’s efforts can have benefits for state and local governments and the private sector, S&T should focus on meeting the needs of DHS components first and foremost.
- Formalize relationships between S&T and other components. To better coordinate research and meet component needs, Congress should more formally connect S&T with research and requirement-setting activities that define what exactly is needed from S&T research. At a high level, this means the creation of a formal oversight council or process to ensure that S&T and relevant parties share visibility and understanding of research projects. At a lower level, this means expanding initiatives, such as Apex programs, which involve integrating component staff in the S&T R&D process to increase research usefulness to end-users.[262]
- Expand the SAFETY Act. One way to support the development of products that support end-user needs is to expand the SAFETY Act, since profit is a good incentive for developing products and services that meet user needs. By expanding the SAFETY Act’s protections in a reciprocal nature with other nations, the U.S. will have access to even more lifesaving technologies. Congress should start a pilot program with a willing ally, such as Israel, to work out the details.
To fund these activities, the Heritage budget recommends $750 million for S&T.
Heritage also recommends:
- $350 million for the Domestic Nuclear Detection Office, and
- $130 million for the Office of Health Affairs.
Making DHS Work for America
As threats of terrorism, cyber espionage, and cyberattacks grow, the U.S.’s immigration system continues to erode, trade and travel continue to expand, and natural disasters remain an ever-present reality, the U.S. must demand significant reform to the Department of Homeland Security. Such reforms are necessary to ensure the safety and security of the U.S. homeland—and they must take place amidst the reality that the current level of federal spending is unsustainable. With annual deficits in the hundreds of billions of dollars in addition to $18 trillion in federal debt, and with entitlements, welfare programs, and interest payments consuming two-thirds of the budget in FY 2014 and growing, all spending must be carefully reviewed. While reforms to the main drivers of U.S. debt—entitlement and welfare programs—are long past due, it is crucial that Congress focus on and prioritize DHS spending.
The Heritage Foundation’s alternative budget is both fiscally responsible and makes the U.S. more secure and prepared by focusing on DHS’s priorities. Reforms to FEMA can save money immediately and other reforms to FEMA, the TSA, and other agencies will yield longer-term savings. Some of the funding saved through reforms will be redirected to priorities such as the Coast Guard, cybersecurity, counterterrorism, and immigration-law enforcement. This budget also does its part to fix the U.S.’s fiscal woes by reducing spending by about $2 billion from FY 2016, a 3 percent decrease.
While cutting spending is rarely a popular idea, these cuts redirect funding to more critical activities and, combined with the policy reforms in this Special Report, improve DHS operations. In other words, if implemented, these recommendations and funding priorities will do more with less. The Heritage budget does its part to improve the U.S.’s fiscal health and make America safer and more secure.
These reforms cannot wait.
—David Inserra is a Policy Analyst for Homeland Security and Cyber Security in the Douglas and Sarah Allison Center for Foreign and National Security Policy, of the Kathryn and Shelby Cullom Davis Institute for National Security and Foreign Policy, at The Heritage Foundation.