Piracy is a growing threat to global commerce and is becoming a U.S. security issue, especially with the pirates’ growing ties to international terrorism. Not only have ransom payments to pirates funded expanding piracy off the coasts of Somalia and driven up the costs of maritime commerce, but they may be supporting terrorist activities in the region and elsewhere as well.
At the very least, piracy is helping to perpetuate the lawlessness in Somalia. In February 2011, piracy took a deadly turn when Somalia pirates hijacked a yacht off Somalia and then killed the four people onboard—all of them Americans.1 Anti-piracy efforts to date have achieved some success, particularly in the Strait of Malacca, but they have failed to halt the spread of piracy in the Gulf of Aden and the Indian Ocean.
The U.S., in cooperation with other seagoing nations—an anti-piracy “coalition of the willing”— needs to move beyond defensive measures and start taking the fight to the pirates, attacking every aspect of the pirate networks. The U.S. and other countries should use every means at their disposal to deny the pirates any safe haven—geographical, financial, or legal—and bring them to justice wherever it is most convenient.[1]
The Scourge of Modern Piracy
Piracy has reemerged as a global concern in recent years. Since 2003, the number of pirate attacks has escalated rapidly. In the past decade, pirate attacks have become commonplace in the Gulf of Aden off Somalia and in the Strait of Malacca between Malaysia and India. Not coincidentally, both are chokepoints on critical sea routes. Attacks have also been reported off the coasts of Bangladesh, Nigeria, Haiti, Colombia, Peru, and Brazil among other places around the world.[2]
Although pirates do not seize a large number of ships, the frequency of attacks and attempted attacks has increased significantly in recent years, especially off the Somali coasts. Hostage taking of both people and ships has become a particularly profitable industry for the Somali pirates. As of February 2011, “685 seafarers of various nationalities are being held for ransom on board 30 ships under various flags at various locations off the extensive Somali coastline—reflecting a situation, which has progressively worsened over the last 12 months.”[3]
Piracy facilitates criminal activities in the country in which the pirates are based. It promotes lawlessness, instability, and supplies people—including terrorists—with the means of continuing and expanding their crimes through the trading and trafficking of illegally obtained materials.
Economic Costs. On April 13, 2010, President Barack Obama signed an executive order identifying Somali piracy as “an unusual and extraordinary threat to the national security and foreign policy of the United States.”[4] Approximately 80 percent of global commerce is transported by sea.[5] Maritime commerce is an increasingly important component of the global economy and is the backbone of just-in-time international trade, as exemplified by large container ships that move between megaports.
For example, oil accounts for approximately 10 percent of maritime commerce off Africa’s coasts.[6] West African oil production is expected to increase and account for 25 percent of U.S. oil imports by 2015. As of 2010, countries in the Gulf of Guinea region were losing approximately $1 billion in oil annually due to piracy.[7] This has, of course, affected world oil prices.
In addition to oil tankers, pirates target other types of ships, including trawlers, chemical transports, general cargo ships, bulk carriers, and sometimes even tugboats and barges.[8] Yachts and ferries have rarely been attacked, at least until recently.[9]
The amount of piracy around the world heavily influences which shipping routes are used, particularly in the Gulf of Aden, which is part of a key shipping route between Saudi Arabia and North America (and Europe) via the Suez Canal. Routing ships around Africa adds 2,700 miles to the journey, exacting sizable costs in time and money. Consequently, more than 20,000 ships pass through the Gulf of Aden each year. Rerouting a ship around Africa costs “an estimated additional $89 million annually, which includes $74.4 million in fuel and $14.6 million in charter expenses,” but this does not include the costs imposed by longer transit times, which reduce the number of voyages a ship can make.[10]
Finding reliable numbers on the costs of piracy is difficult because many hijacked cargo ships go undocumented. Shipping companies are understandably reluctant to provide detailed information because they do not want the negative attention. The available estimates are based on incomplete data at best. The daily maritime newspaper Lloyd’s List estimates that piracy costs the maritime shipping industry $16 billion annually.[11]
While many ships are robbed of their cargo, some of which is later sold, much of the money that pirates collect comes from ransoms. Many pirate communities around the world do not demand ransom payments and instead just take the cargo, but Somali pirates typically “ask” for ransoms, and their ransom demands have been escalating. In 2009, the average ransom demanded by Somali pirates was about $2 million per ship, but in early 2010, the pirates were paid ransoms of $3 million and $7 million.[12] As of November 2010, the highest ransom was the $9 million to $9.5 million paid for a South Korean oil tanker.[13] An estimated $50 million in ransoms was paid in 2008,[14] and an estimated $75 million was paid for the release of 21 ships in 2010.[15]
Furthermore, cargo insurance is a significant part of a shipping company’s operational costs, and the increased frequency of pirate attacks has prompted insurance companies to raise insurance rates for ships transiting high-risk areas. For example, insurance rates for ships traveling through the Gulf of Aden are about five times standard war-risk rates.[16]
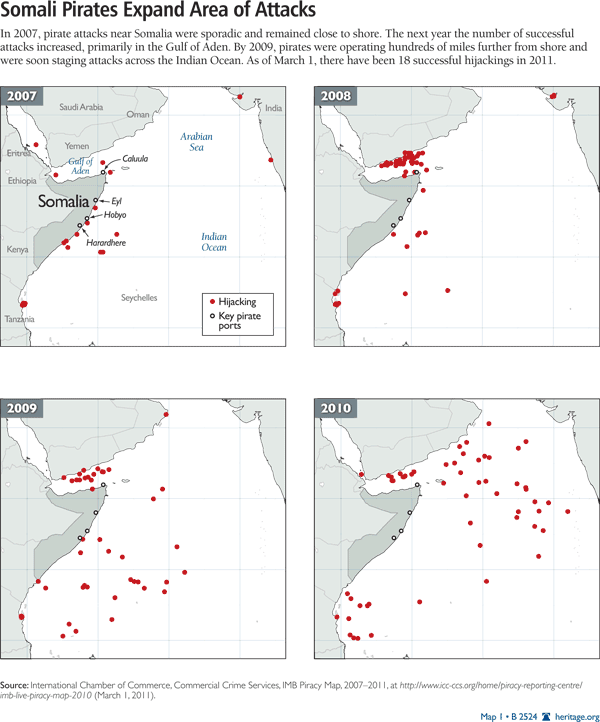
Somali Pirates. The Somali pirates are based in the failed state of Somalia and operate in the Gulf of Aden and the Indian Ocean. Since the U.N. pulled out of Somalia in March 1995, the country has lacked a central government that the Somali people recognize as legitimate. The lawlessness has continued with pirates playing a key role. Most of the major pirate bases of concern are in Somalia, particularly the port city of Eyl, which is in the northeastern Puntland region.[17] There is also activity in Harardhere in central Somalia, but increased U.N.-authorized naval patrols in the region have led to a decline in the number of pirate attacks in this area.
The pirates have adapted to these increased security measures by shifting tactics. For instance, as international shipping companies began to reroute ships away from the coasts of Somalia, pirates have expanded their operations north to the Gulf of Aden, as far south as the Mozambique Channel and the Seychelles, and to the east toward India.[18] (See Map 1.) An estimated 1,000 armed pirates comprising former militiamen and fishermen are working in the Gulf of Aden and the western Indian Ocean.[19]
The Somali pirates’ one “good” characteristic is that they have generally avoided bloodshed. In 2008, only four mariners were killed, and another 14 are presumed dead or missing. While fatalities sometimes occur, crews of hijacked ship are rarely harmed.
However, the pirates seem recently to have changed their policy. In response to the sentencing of a Somali pirate to 33 years in prison for his role in the 2009 hijacking of the Maersk Alabama,[20] a pirate identified as Muse Abdi has stated that the pirates have changed their rules to allow the killing of hostages: “It will never ever happen that hostages are rescued and we are hauled to prison.” The February 18 killing of four American hostages on the yacht S/V Quest off Somalia[21] seems to confirm this shift to more cold-blooded tactics.
Terrorist Nexus
While the lawlessness in Somalia is troubling, activities in the Horn of Africa are of increasing international concern. In addition to aiding in lawlessness and other enterprises, it is thought that pirates are also supporting extremist organizations operating in northern and western Africa.
Al-Qaeda leaders and publications clearly state that al-Qaeda seeks to “oppose peacekeeping efforts in Muslim countries, notably Somalia and Sudan,” and harm the global economy by disrupting oil production. Furthermore, “Somalia has long been a rear base for the East Africa al Qaeda (EAAQ) cell” that conducted the successful 1998 attacks on U.S. embassies. Rather than basing “its primary leaders or principal training camps” in Africa, al-Qaeda has established ties with local Islamist groups. Hizbul Islamia, a splinter group from Somali terrorist group Al-Itihad al-Islamia (AIAI), is “seeking to establish an Islamist state in Somalia.” Harakat al-Shabab, another AIAI splinter, has been working with EAAQ to establish an Islamic state in the Horn of Africa.[22]
At first glance, the terrorist and pirate activities may seem unrelated, but terrorist organizations benefit from pirates in many ways. Al-Shabab benefits from the goods and weapons that pirates smuggle into various Somali ports. Somalia is also a port of entry into Africa for foreign fighters and a transit point for terrorists traveling to other countries, including those responsible for the March 2009 bombing in Yemen.[23]
In turn, Islamist groups permit pirates to operate in Islamist-controlled areas. Pirates use the proceeds from hijacking and pilfering ships to pay suppliers. Potential terrorists and criminals use pirates not only as a means of transportation, but also as a source of financing[24] and materials (e.g., weapons, drugs, and other materials in hijacked ships) that terrorists find useful.
Some experts have argued that these illegal organizations can operate in such proximity without cooperating to a significant degree and developing strong ties.[25] In contrast, Admiral Mark Fox, Commander of U.S. Naval Forces Central Command, has observed:
Al-Shabab is responsible for a lot of training activity and camps and that sort of thing in Somalia…. The pirates use these things. There cannot be a segregation between terrorist activity, in my mind, and counter piracy. We can’t be passive and hopeful it doesn’t happen.[26]
Pirate Tactics
Somali pirates often go to sea in a “mother ship,” which is usually a fishing vessel captured in a previous pirate attack. The mother ship enables the pirates to stay at sea longer and operate further away from Somalia than if they just used their skiffs. Earlier in this decade, they often used skiffs to launch attacks from land. The pirates also use the mother ship to scout for targets of opportunity.
Once a passing cargo ship has been spotted, the mother ship deploys two to four smaller high-speed vessels (skiffs), which flank the target and approach at high speed. To slow or stop the ship, pirates use various means of intimidation, including firing automatic weapons and rocket-propelled grenades. Once the target has slowed, a team of seven to 10 pirates boards the ship using ladders and grappling hooks and takes the ship and its crew hostage. The team of pirates is usually armed, and the small number of crewmen required to operate modern merchant ships (usually no more than a dozen) makes hijacking a ship relatively easy.
Once hijacked, larger cargo ships and their crews are often sailed to a pirate port in Somalia to await negotiation and payment of their ransom. Pirates also maintain networks of depots along coasts, where they can sell captured goods, rearm, and resupply their ships. The network of depots also affords them the opportunity to communicate with spies in the region to obtain information about ships that may be passing through the area.
Profits from hijacked cargo are disbursed to the pirate suppliers, organizers, and investors who support the pirates during their time at sea. The illegal income may also benefit their clan members, including family and friends. The profits from piracy support the local economy, filtering through the community as pirates resupply and upgrade their vessels and weapons and as those in the network spend their wages.
Current Counterpiracy Efforts
Modern efforts to suppress piracy have met with mixed success. Piracy in the Strait of Malacca has declined significantly, but the Somali pirates have expanded their operations.
The Strait of Malacca. In 2004, there were 38 recorded pirate attacks in the Strait of Malacca, but only two incidents were reported in 2008 and another two in 2009.[27] This is an example of successful regional cooperation and public–private cooperation under the Regional Cooperation Agreement on Combating Piracy and Armed Robbery Against Ships in Asia. Sixteen nations participate in that regional operation.
Gulf of Aden and the Western Indian Ocean. Piracy off Somalia has proven more difficult to address because the failed state of Somalia provides the perfect base from which to mount pirate activities. Local law enforcement is either nonexistent or powerless against the Somali pirates, and international law largely protects the pirates from outside interference while on land. Compared with pirates in the Strait of Malacca, the Somali pirates also have much more room to operate, from the Suez Canal to the west coast of India.
There are currently three major multinational anti-piracy missions near the Horn of Africa. Since November 2008, the European Union’s Operation Atalanta has protected World Food Program vessels delivering food to Somalia and other ships in the region. NATO’s Operation Ocean Shield has deployed warships in the region with a mandate to protect shipping until the end of 2012. Finally, Combined Task Force 151, a multinational task force established in January 2009, patrols the Gulf of Aden and the east coast of Somalia.
Even the U.N. Security Council has acknowledged the threat of Somali piracy and has repeatedly extended authorization for U.N. member states and regional organizations to take “all necessary means to repress acts of piracy and armed robbery at sea” in Somali territorial waters.[28] This authorization for other states to violate the territorial waters of another state marks an unusual step and is de facto recognition that Somalia has no functioning government to control its territory.
The Legal Environment
Under customary international law, countries have long exercised universal jurisdiction over acts of piracy on the high seas: “As therefore [a pirate] has renounced all the benefits of society and government, and has reduced himself afresh to the savage state of nature, by declaring war against all mankind, all mankind must declare war against him.”[29] Essentially, any country can legally act against pirates outside national territorial waters, regardless of the pirate’s “nationality” and the nationality of the vessel attacked by pirates. The U.S. Constitution specifically authorizes Congress to “define and punish piracies and felonies committed on the high seas, and offenses against the law of nations.”[30] In fact, piracy was a major impetus for the development of international law, the body of rules and customs that guide relations between countries.
The 1982 U.N. Convention on the Law of the Sea (UNCLOS) generally codified this understanding of universal jurisdiction and even expanded the definition of piracy, but in some ways it has complicated enforcement. “In the classic law of nations, pirates were simultaneously criminals and military enemies.”[31] At sea, a pirate could be attacked and killed but was also subject to capture and trial by law, unlike a prisoner of war. Yet commonly accepted interpretations of UNCLOS and Article 3 of the Geneva Conventions have turned this historical practice on its head, providing “pirates today [with] the protections of criminal defendants, as well as some of those of enemy prisoners, without the disabilities of either.”[32]
This has complicated the legal environment to the point that many foreign navies are reluctant to take pirates prisoner, much less prosecute them. In the first six months of 2010, EU and NATO naval forces captured and then released an estimated 700 pirates.[33] More recently, Denmark released six pirates, who were captured attacking the container ship Elly Maersk, because “there was not enough evidence for a conviction in a Danish court.”[34] This legal vacuum, in part, explains why Russia set 10 pirates adrift in the Indian Ocean on the flimsy excuse that it lacked “sufficient legal grounds to detain them.” The freed pirates are presumed to have died at sea.[35]
Taking the Fight to the Somali Pirates
A defensive strategy of trying to protect every ship that passes through high-risk zones, particularly in the Gulf of Aden and the western Indian Ocean, will almost certainly fail because there are too many vulnerable ships, too few law enforcement and military assets to protect them, and too many pirates. Furthermore, modern pirates, especially those based in Somalia, have demonstrated an impressive ability to adapt to and exploit the changing security environment.
Exploiting the Pirates’ Vulnerabilities. To end the piracy threat off the Horn of Africa and in the western Indian Ocean, the U.S. and other countries should use their strengths to attack the Somali pirates at their weak points, including the pirates’ profits, bases of operations, and manpower.
Money. The expansion of piracy is being driven by profit, whether that profit is sought for personal gain or for ideological reasons (e.g., financing terrorism). If piracy were not profitable at an acceptable level of risk to the pirates, there would be little or no piracy. Accordingly, the U.S. and other countries should strongly discourage the payment of ransoms and use all available tools of government to disrupt the pirates’ financial transactions. Most of the ransom money that enters Somalia will eventually leave the country in some form to purchase goods unavailable in Somalia.
Consequently, the U.S. and other countries should try to make extracting ransoms, selling captured cargoes, and keeping the ransom money and proceeds of the sales increasingly difficult and expensive. If they succeed, the pirate enterprises will eventually respond to the changing economic incentives either by disbanding or by finding other more lucrative or less dangerous criminal activities.
Means. Piracy requires viable targets, pirate ships, and pirate ports. Pirates operate in the gaps in maritime enforcement, whether such enforcement is conducted by regular law enforcement or naval forces. By implementing basic, nonlethal defensive measures, the crew of a commercial ship can make its capture much more difficult. Even delaying capture dramatically increases the risk to the pirates by allowing naval forces to converge on pirates attacking the ship.
The mother ships that Somali pirates use are another potential weak point. Although a mother ship may initially appear to be an innocent commercial vessel, this facade will likely collapse under closer examination. A ship towing several skiffs or carrying the unique tools of piracy (e.g., weapons, grappling hooks, and hook ladders) is probably a pirate ship.
Somali pirates generally operate out of four Somali port towns: Caluula, Eyl, Hobyo, and Harardhere.[36] These are geographical bottlenecks in pirate operations that anti-piracy forces can and should exploit.
Men. The nations of the world need to make piracy a riskier, more dangerous, and less profitable occupation. If potential recruits know that they run an increasingly high risk of never returning home, they will be less willing to join, and current pirates will be more inclined to retire while they are still alive and can enjoy their loot.
Selective targeting of pirate leaders, à la Predator attacks on terrorist leaders in Afghanistan and Pakistan, might also prove useful in persuading pirates to reconsider their career choices.
Knowing the Enemy. Much is already known about the pirate gangs operating out of Somalia. However, the U.S. and other countries need to expand both their situational awareness in the Indian Ocean and their understanding of how the pirates operate, especially as they react to new anti-piracy initiatives. Among other assets, unmanned aerial vehicles (UAVs), satellites, signals intelligence, human intelligence, and interrogations of captured pirates can help to fill in the knowledge and coverage gaps.
Additional Considerations
The problem of piracy offers no easy solutions. If it did, it would probably have ceased to be a problem given the assets that have already been deployed.
Hostages. The multinational forces should take reasonable precautions to avoid endangering the hundreds of hostages held by the Somali pirates. For example, direct attacks on pirate ports and depots along the coast are inadvisable because of the high probability of heavy casualties among hostages and civilians.
However, the U.S. and other countries should not allow the existence of hostages to dictate their responses to piracy. They should continue to look for opportunities to rescue hostages without killing hostages or civilians.
Captured Pirates. One of the most difficult challenges in combating piracy is dealing with captured pirates. Russia’s elegantly simple solution of setting them adrift at sea is not a viable option for the U.S. or EU countries. Until recently, Kenya had signed agreements with the United Kingdom and the U.S. to accept custody and try pirates. However, in 2010, Kenya stopped accepting custody of pirates.[37]
Preferably, pirates would be tried in nearby countries or on board ships. Until Somalia has a viable government, most pirates should be prosecuted and imprisoned by other countries in the region. Judicious use of international aid to support these countries would be a good investment that would strengthen law and order in the region while dramatically reducing enforcement costs.
A Long-Term Solution. While the U.S. and its allies can make a pirate’s life more difficult and shorter, the long-term solution to Somali piracy is to establish effective governance of Somali territory and territorial waters. Without safe havens from which to operate, most piracy would probably disappear.
In Somalia, efforts to build a functioning central government from the top down have failed by all accounts. Instead, efforts to bring order to Somalia should start small and work up. Building government up from the grassroots in Somalia offers some hope, but it will be long-term project.[38] However, the disruption of piracy will severely disrupt the remains of the Somali economy, particularly since piracy has been one of the few growth industries in Somalia in recent years. When piracy collapses, it will affect many Somalis who are not directly involved in piracy and complicate matters for any nascent Somali government. Rebuilding the Somali economy will take time.
Taking the Fight to the Pirates
In the short term, the U.S. and other states should:
- Deny the pirates any safe haven—geographical, financial, or legal. As a general principle, the U.S. and other countries should use every available asset and opportunity—within reason—to destroy, capture, deter, and generally harass pirates in all aspects of their profession. Specifically, the U.S. rules of engagement should be adjusted to allow and encourage U.S. forces to engage pirate forces, including sinking pirate ships, whenever U.S. forces have the opportunity and the advantage. As Admiral Fox has recommended, the U.S. should essentially apply the counterterrorist approach to the pirates.[39] This must include ending the “catch and release” policies practiced by EU and NATO naval forces.
- Encourage shipping companies and insurance companies to implement best management practices to deter or delay pirates from boarding and seizing ships. The International Maritime Organization’s Maritime Safety Committee regularly updates the guidelines for ships transiting the high-risk area off the Somali coasts. Simple and relatively inexpensive measures, such as transiting the area at a minimum speed of 18 knots, evasive maneuvering to deter and delay boarding, and erecting physical barriers (e.g., razor wire and electrified fences), have proven effective. Immediately alerting nearby law enforcement and military units of any attempted attack would further limit the pirates’ effectiveness.[40]
- Discourage the payment of ransoms to pirates. Ransoms are the lifeblood of Somali piracy. Payment of ransoms encourages and finances further pirate attacks. The U.S. and other countries should discourage shipping companies from paying ransoms.
- Continue and expand the current coalition of the willing that is patrolling the waters off Somalia. Combined Task Force 151, NATO’s Operation Ocean Shield, and the EU’s Operation Atalanta have enjoyed some limited successes. The U.S. should work to expand and coordinate cooperation in the region. The piracy threat in the Indian Ocean provides a unique opportunity for the U.S. military to work together with the Indian, Chinese, and Russian navies toward a common goal. The U.S. should consider proposing a multinational blockade of select Somali ports to examine every ship leaving or entering those ports. Any ships and crews suspected of involvement in piracy should be detained or tracked.
- Use intelligence and reconnaissance assets to identify, track, and map pirate activities and their supporting networks. As the multinational forces gain a clearer picture of pirate activity, they should be able to use the available forces to greater effect. The pirates have demonstrated the ability to adapt to changes in the security situation, so the intelligence-gathering effort should be maintained until the threat has abated.
- Work with countries in the region to prosecute and imprison pirates in the region to limit enforcement costs. Judicious use of international aid to assist the legal and judicial systems of countries will likely pay huge dividends, both in combating piracy and in strengthening law and order in the region.
- Recognize that effective U.S. and international action against the pirates will incur the wrath of some human rights nongovernmental organizations, international lawyers, and even some countries. The U.S. and other countries should also recognize that more effective, aggressive enforcement will likely result in casualties among hostages and other civilians. Ending the threat of piracy will require firm political will in the White House to follow through on anti-piracy policies until the threat is eliminated.
Over the longer term, the U.S. should:
- Review U.S. piracy law and update it as needed to clarify legal definitions and jurisdiction, establish rules of evidence, and streamline the judicial process.[41] Congress may want to consider explicitly extending the Uniform Code of Military Justice to cover pirates, specifically availing the U.S. of the “at sea” exception that allows trials by court-martial on U.S. military ships or bases. Such legal proceedings would limit “the logistical and political costs of transporting them from the Indian Ocean.”[42]
- “Unsign” the U.N. Convention on the Law of the Sea, both to combat piracy effectively and to protect other U.S. national interests by ending any U.S. obligation to avoid violating the object and purpose of UNCLOS.[43]
Conclusion
Piracy has become a serious threat to international commerce, and the Somali pirates have been developing ties with Islamist terrorists in the region. Admiral Fox has the right idea in treating the pirates as terrorists and going after them, their supply lines, and their financial transactions with “the same intensity [the coalition members] use when targeting terrorists.”[44]
—James Jay Carafano, Ph.D., is Deputy Director of the Kathryn and Shelby Cullom Davis Institute for International Studies and Director of the Douglas and Sarah Allison Center for Foreign Policy Studies, a division of the Davis Institute, at The Heritage Foundation. Jon Rodeback is Research Editor at The Heritage Foundation. Meghan L. Tucker, a freelance writer and researcher in Washington, D.C., assisted in researching and writing this paper.